Astaroth is a Trojan and information stealer of sensitive information such as user credentials using a key logger module, operating system calls interception and clipboard monitoring. It is used in a fileless malware campaign in the memory of infected computers detected by Microsoft Defender ATP Research Team researchers.
Astaroth is also known for abusing living-off-the-land binaries such as the command line interface of the Windows Management Instrumentation Command-line to stealthily download and install malware payloads in the background.
How does Astaroth Trojan Work
As with many traditional campaigns, this campaign begins with a .7zip file that gets downloaded to the user machine through a mail attachment or a mistakenly-pressed hyperlink. The downloaded .7zip file contains a .lnk file that, once pressed, initializes the malware. Upon initialization, a process spawns that uses the legitimate wmic.exe to initialize an XSL Script Processing attack. This attack allowed the malware to communicate with a remote C2 server and sent information like location information about the infected machine to the remote server.
The remote XSL script contains highly obfuscated code that is able to execute an additional malicious activity. It uses several functions to hide its activities from antivirus defenses and researchers. This script is ultimately responsible for the malicious use of BITSAdmin to download the attacker’s payload to the target from a separate C2 server. The payload files are masqueraded as JPEGs, GIFs, and extensionless files, and contain the Astaroth Trojan modules.
Once the payload is received, it identifies if Avast exists on the infected machine. If so, it uses Avast to load a malicious module responsible for loading other modules and gathering information about the machine. A second module is loaded to collect and exfiltrate information like clipboard data, password information, and more.
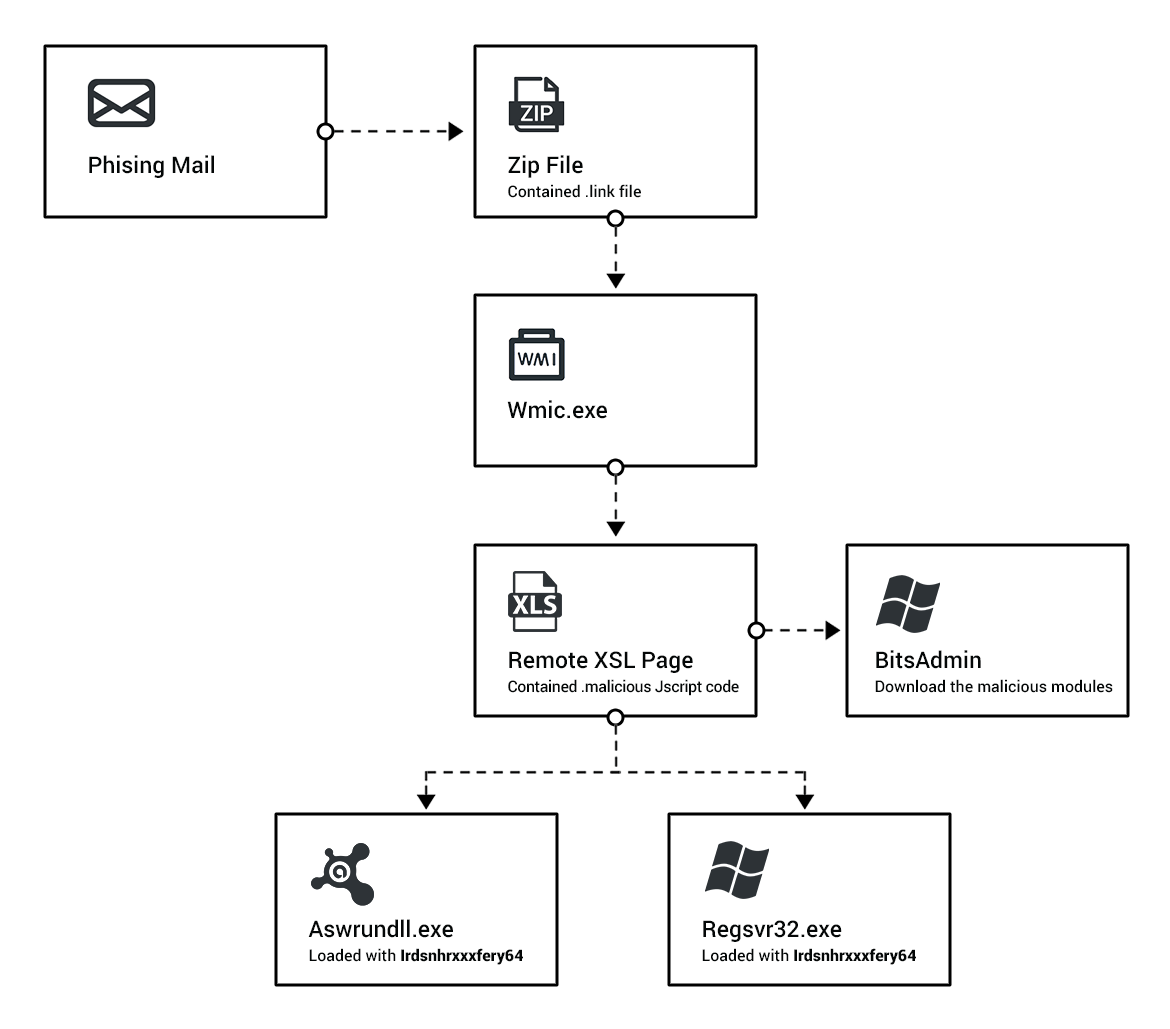
Figure: Astaroth infection breakdown
How to avoid installation
To prevent these computer infections, be very cautious when browsing the internet. Think twice before opening email attachments. Files that seem irrelevant and those received from suspicious/unrecognizable email addresses should never be opened. These should be deleted without reading. Furthermore, bear in mind that criminals often send deceptive messages claiming that the recipient will gain something free of charge (e.g., the recipient has won a lottery, received a package, someone has transferred money to the recipient’s account, etc.). They hope that the recipient will be tricked into opening the attachment. Do not be fooled by this scam. Having a reputable anti-virus/anti-spyware suite installed and running at all times is also paramount. These tools commonly detect and eliminate malware before it can harm the system. The main reasons for computer infections are poor knowledge and careless behavior. The key to safety is caution. If you believe that your computer is already infected, we recommend running a scan with Spyhunter for Windows to automatically eliminate infiltrated malware.
Summary
| Name | Astaroth Malware |
| Threat Type | Trojan, Password Stealing virus, Banking Malware, Spyware |
| Anti-virus Detect | Avast, BitDefender, ESET-NOD32, Kaspersky, Full List of Detection names in VirusTotal |
| Symptoms | Trojans are designed to stealthily infiltrate victim’s computer and remain silent thus no particular symptoms are clearly visible on an infected machine. |
| Distribution Methods | Infected email attachments, malicious online advertisements, social engineering, software cracks. |
| Danger Level | High (Trojans are often used as a backdoor for Ransomware) |
| Damage | Stolen banking information, passwords, identity theft, victim’s computer added to a botnet. |
| Removal | To eliminate Astaroth virus recommend scanning computer with Spyhunter. |
