Retadup is a Trojan that targets the Windows platform. It is reported that this malware is used for targeted attacks and some variants of the malware come with Keylogger, screen capture, and password-stealing capabilities. The malware is used to mine cryptocurrency on the infected system. It communicates with its remote control server and accepts commands to execute on the infected system. In August 2019, 850,000 infected hosts were cleaned remotely in an operation of the French police. The notorious Retadup malware infects computers and starts mining cryptocurrency by sapping power from a computer’s processor. Although the malware was used to generate money, the malware operators easily could have run other malicious code, like spyware or ransomware. The malware also has wormable properties, allowing it to spread from computer to computer. Since its first appearance, the cryptocurrency mining malware has spread across the world, including the U.S., Russia, and Central and South America.
The Retadup malware, the target of the operation, has spread around the world but was particularly active in South America. It infects computers and uses their processing power to mine for cryptocurrency without the knowledge of the device’s owner. This malware was particularly concerning because it is “wormable,” meaning it can propagate from one computer to another. The police were able to hijack the malware after the Avast security firm discovered a flaw in its command and control (C&C) server. Although Avast is headquartered in the Czech Republic, it contacted the French police as most of the servers hosting the malware were located in France. Avast described the process of identifying the flaw, passing this information to the police, and instructing the police on how to repurpose the botnet to turn the C&C server into a disinfection server in a blog post. By taking over the C&C server and using it to distribute a malware removal script, the police could remove the malware from users’ computers automatically, with no user action required.
Retadup is a malicious worm affecting Windows machines throughout Latin America. Its objective is to achieve persistence on its victims’ computers, to spread itself far and wide and to install additional malware payloads on infected machines. In the vast majority of cases, the installed payload is a piece of malware mining cryptocurrency on the malware authors’ behalf. However, in some cases, we have also observed Retadup distributing the Stop ransomware and the Arkei password stealer.
The security firm got involved after it discovered a design flaw in the malware’s command and control server. That flaw, if properly exploited, would have “allowed us to remove the malware from its victims’ computers” without pushing any code to victims’ computers, the researchers said. The exploit would have dismantled the operation, but the researchers lacked the legal authority to push ahead. Because most of the malware’s infrastructure was located in France, Avast contacted the French police. After receiving the go-ahead from prosecutors in July, the police went ahead with the operation to take control of the server and disinfect affected computers. The French police called the botnet “one of the largest networks” of hijacked computers in the world.
The operation worked by secretly obtaining a snapshot of the malware’s command and control server with cooperation from its web host. The researchers said they had to work carefully as to not be noticed by the malware operators, fearing the malware operators could retaliate.“The malware authors were mostly distributing cryptocurrency miners, making for a very good passive income,” the security company said. “But if they realized that we were about to take down Retadup in its entirety, they might’ve pushed ransomware to hundreds of thousands of computers while trying to milk their malware for some last profits.”With a copy of the malicious command and control server in hand, the researchers built their own replica, which disinfected victim computers instead of causing infections.
“The police replaced the malicious [command and control] server with a prepared disinfection server that made connected instances of Retadup self-destruct,” said Avast in a blog post. “In the very first second of its activity, several thousand bots connected to it in order to fetch commands from the server. The disinfection server responded to them and disinfected them, abusing the protocol design flaw.”In doing so, the company was able to stop the malware from operating and remove the malicious code to over 850,000 infected computers. Jean-Dominique Nollet, head of the French police’s cyber unit, said the malware operators generated several million euros worth of cryptocurrency. Remotely shutting down a malware botnet is a rare achievement — but difficult to carry out.
Version of Retadup
Several years ago the U.S. government revoked Rule 41, which now allows judges to issue search and seizure warrants outside of their jurisdiction. Many saw the move as an effort by the FBI to conduct remote hacking operations without being hindered by the locality of a judge’s jurisdiction. Critics argued it would set a dangerous precedent to hack into the countless numbers of computers on a single warrant from a friendly judge. Since then the amended rule has been used to dismantle at least one major malware operation, the so-called Joanap botnet, linked to hackers working for the North Korean regime.
Further analyzing and correlating them based on their C&C protocol and our own RETADUP detections. These indicate that, at least for now, RETADUP’s operators — despite their history in deploying their malware in targeted attacks — are focusing on cybercriminal cryptocurrency mining.
| WORM_RETADUP.A | WORM_RETADUP.D | WORM_RETADUP.G | |
| Scripting Language | AutoIt | AutoIt | AutoHotKey, with some components in AutoIt |
| Propagation | Worm spawns LNK files, propagates in removable drives | Worm spawns LNK files, propagates in removable drives | Worm spawns LNK files, propagates in removable drives |
| Main Payloads | Information stealer | Cryptocurrency-mining bot | Cryptocurrency-mining bot |
| Related Tools | Android backdoor | Browsing history viewer | |
| Campaign | Cyberespionage | Cybercrime | Cybercrime |
Figure 1. Comparison of RETADUP’s versions
Shifting to AutoHotKey
RETADUP’s AutoHotKey version bears considerable resemblance to its AutoIt variant in terms of the endgame (cryptocurrency mining) and the baselines it uses — the techniques it employs to propagate, evade detection, and install the malicious Monero miner. Apart from the apparent convenience of abusing open-source software, the shift to using AutoHotKey is most likely because of its novelty as a scripting language. This entails the lack of known or prevalent tools that can actively detect and analyze malware written in AutoHotKey.
This is exacerbated by the polymorphism (replicating slightly different versions of itself to avoid one-to-one detection) we observed in RETADUP’s AutoHotKey version. The AutoIt-based variants don’t have this feature as they used AutoIt 3-compiled scripts (.a3x), so they’re compressed and encrypted.
Alternatively, AutoHotKey is dropped and installed if the system didn’t originally have one. It still uses a link/shortcut file (LNK) as its primary launcher, but it now also creates a scheduled task for persistence and privilege escalation.

Figure 3. Components of RETADUP’s AutoHotKey version
The command it executes to create a scheduled task is:
schtasks /create /sc minute /mo 1 /tn bqspogcjposfemiigrgmk /tr
“C:\bqspogcjposfemiigrgmk\bqspogcjposfemiigrgmk.exe C:\BQSPOG~1\BQSPOG~1.TXT”

Figure 4. Scheduled task created by RETADUP
The malicious AutoHotKey script is not compiled, so its authors used some form of obfuscation and polymorphism to help evade detection. The main form of obfuscation employed involves converting string constants (raw values) into hex bytes. During propagation, the malware will append and prepend a line of commented-out alpha string to dropped copies of the script. It also changes every function’s name so each copy of the malware has a different hash.
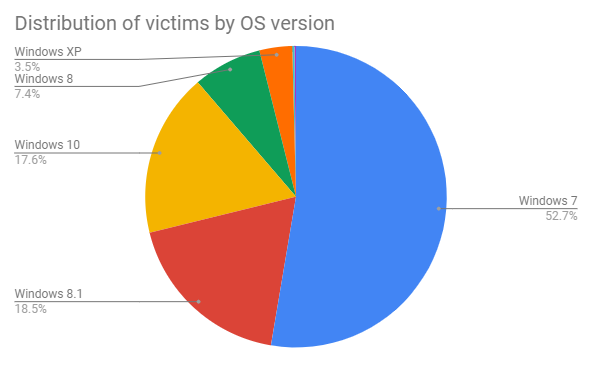
The Retadup bots sent quite a lot of information about the infected machines to the C&C server. Since we had limited access to a snapshot of the server, we were able to obtain some aggregated information about Retadup’s victims. The most interesting piece of information for us was the exact amount of infections and their geographical distribution. To date, we have neutralized over 850,000 unique infections of Retadup, with the vast majority located in Latin America. Since the malware authors mined cryptocurrency on the victims’ computers, they were naturally interested in the computing power of infected machines. We were able to determine that the most infected computers had either two or four cores (the average number of infected computer cores was 2.94) and that the majority of victims used Windows 7. Over 85% of Retadup’s victims also had no third-party antivirus software installed. Some also had it disabled, which left them completely vulnerable to the worm and allowed them to unwittingly spread the infection further. Because we are usually only able to protect Avast users, it was very exciting for us to also help protect the rest of the world from malware on such a massive scale.