Java/Adwind is typically spread as an executable file attached to spam email messages. When the file attachment is launched, the archive file drops malicious components onto the system, then continues to run in the background. On a Windows machine, the components are dropped to the %AppData% folder. When running in the background, the Adwind archive file serves as a backdoor, able to install other programs, steal user information, log keystrokes, capture screenshots and update its own configuration. Information captured by the backdoor is silently forwarded to a remote server.
What is Adwind?
Adwind RAT, a cross-platform, multifunctional malware program also known as AlienSpy, Frutas, Unrecom, Sockrat, JSocket and just, and which is distributed through a single malware-as-a-service platform. One of the main features that distinguish Adwind RAT from other commercial malware is that it is distributed openly in the form of a paid service, where the “customer” pays a fee in return for use of the malicious program. There were around 1,800 users of the system by the end of 2015. This makes it one of the biggest malware platforms in existence today.
Attackers are targeting entities from the utility industry with the Adwind Remote Access Trojan (RAT) malware via a malspam campaign that uses URL redirection to malicious payloads. Adwind (also known as jet, AlienSpy, JSocket, and Socket) is distributed by its developers to threat actors under a malware-as-a-service (MaaS) model and it is capable of evading detection by most major anti-malware solutions. While the Adwind Trojan manages to avoid detection by some anti-malware solutions, sandbox- and behavior-based antivirus software should be capable of detecting and block it successfully.
What it can do?
The malware’s list of functions includes the ability to:
- collect keystrokes
- steal cached passwords and grab data from web forms
- take screenshots
- take pictures and record video from a webcam
- record sound from a microphone
- transfer files
- collect general system and user information
- steal keys for cryptocurrency wallets
- manage SMS (for Android)
- steal VPN certificates
Who are the victims of its attacks?
Between 2013 and 2016, different versions of the Adwind malware have been used in attacks against at least 443,000 private users, commercial and non-commercial organizations around the world.
Industries of interest for the attacks:
- Manufacturing
- Finance
- Engineering
- Design
- Retail
- Government
- Shipping
- Telecom
- Software
- Education
- Food production
- Healthcare
- Media
- Energy
Am I at risk?
Be aware if you are working in the industries listed above and are located in the following counties: United Arab Emirates, Germany, India, the USA, Italy, Russia, Vietnam, Hong Kong, Turkey, and Taiwan. You are in the group of the highest risk.
What is the process of spreading Adwind Malware
Targets home and enterprise users
This allows its operators to successfully compromise their targets’ computers without raising suspicion, and perform a wide range of malicious tasks from stealing sensitive info like VPN certificates and credentials from Chrome, IE, and Edge to collecting and exfiltrating the victims’ keystrokes. The Adwind RAT can also record video and sound, as well as snap photos using the infected machine’s webcam, as well as mine for cryptocurrency and harvest cryptocurrency wallet information.
Adwind has been making the rounds since 2013, with the RAT being observed in attacks targeting hundreds of thousands of individuals and entities from a large array of industries, including finance, telecom, software, energy, and government among others. From previously detected malicious campaigns distributing it, the initial infection vector most used by most attackers dropping Adwind on their targets’ systems are spam emails that contain infected attachments or links redirecting the targets to the primary payload.
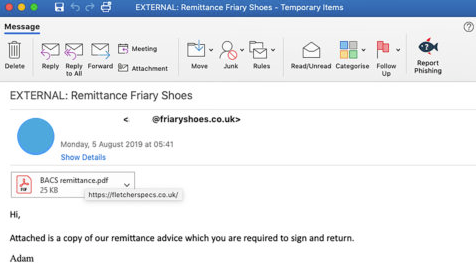
Malicious URLs camouflaged as a PDF attachment
The emails used to infect the victims of this specific campaign were found in the inboxes of staff employed by entities from the utility sector, landing thereafter successfully bypassing the companies’ email gateways. They are being sent via a compromised email account at Friary Shoes, with the company’s servers also being used to store and deliver the Adwind malware payload to the victims’ computers.
“At the top of the email is an embedded image which is meant to look like a PDF file attachment, however, is, in fact, a jpg file with an embedded hyperlink,” found the Cofense researchers who spotted this new Adwind campaign.”When victims click on the attachment, they are brought to the infection URL hxxps://fletcherspecs[.]co[.]uk/ where the initial payload is downloaded.”
To trick the targets into clicking the malicious link disguised as a PDF attachment, the attackers use the following email body: “Attached is a copy of our remittance advice which you are required to sign and return.”
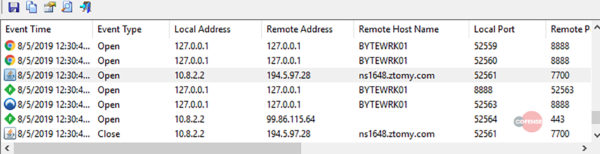
After clicking on the download link included in the malspam message, the initial payload in the form of the Scan050819.pdf_obf.jar JAR file will be dropped on the targeted machine. The malware will immediately contact its command and control (C2) server upon execution and will add all the data it collects together with all its dependencies into the C:\Users\Byte\AppData\Local\Temp\ folder. The next step in the infection chain is to find and kill any well-known analytics and antivirus software with the help of the legitimate taskkill Microsoft utility designed to allow ending one or more processes. Indicators of compromise including malware sample hashes, malicious URLs used in the phishing attacks, and associated are included at the end of the Cofense report.
Switching methods and baits
Cofense’s researchers have also observed several other coordinated attacks employing a large array of techniques and baits to phish various types of targets. Just last week, they spotted a spear-phishing campaign circumventing a Microsoft email gateway with the help of documents shared via the Google Drive service and designed to target the staff of an energy industry company. In July, crooks were seen while switching from the malicious URLs they usually employ to WeTransfer notifications that helped them bypass email gateways developed by Microsoft, Symantec, and Proofpoint. A base HTML element was also used to conceal phishing landing page links from antispam solutions, a tactic that made it possible to evade Office 365 Advanced Threat Protection’s security checks and get their phishing emails into the inboxes of American Express customers. Yet another campaign employing fake eFax messages was detected in early July while infecting targets with a banking Trojan and RAT cocktail using malicious Microsoft Word document attachments. Cofense was also behind the disc behind the discovery of a phishing campaign that abused QR codes one month earlier, through which its operators redirected potential targets to landing pages while dodging security solutions and controls designed to stop such attacks in their tracks.
Where does Adwind malware install, and how?
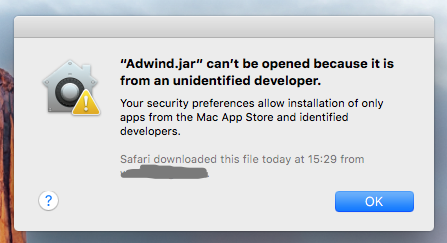
Regardless of the Gatekeeper settings preferences, any user—whether carelessly or intentionally—can override its protection. If a user attempts to execute a file that comes from an unidentified developer (not signed with a valid Apple digital certificate), Gatekeeper will warn the user, but not fully prevent installation if the user skips the warning.
For example, when attempting to run the Adwind RAT file by double-clicking on it, Mac users will see a Gatekeeper alert:
To override Gatekeeper, users could Control-Click or Right-Click on the file.
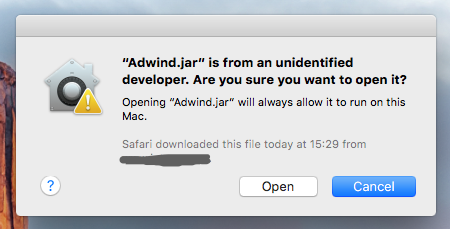
And that’s not the only way to get around Gatekeeper’s protection. Gatekeeper’s quarantine attribute is not applied if a user drops a file locally from one Mac to another; for instance, if you download the Adwind RAT sample on your Mac, unzip the password-protected archive, and then drop the file to a remote Mac in your LA
