A new ransomware has been spotted over the weekend, carrying references to the Russian president and antivirus software. The researchers call it Nemty.This is the first version of Nemty ransomware, named so after the extension it adds to the files following the encryption process.A new ransomware, called Nemty ransomware, has been discovered over the weekend by malware researchers. The name of the ransomware comes after the extension it adds to the encrypted file names, the malicious code also deletes their shadow copies to make in impossible any recovery procedure.
What is NEMTY PROJECT?
NEMTY PROJECT is a high-risk ransomware-type infection discovered by malware researcher S!Ri. The purpose of this ransomware is to encrypt most of stored files so that developers could make ransom demands by offering a paid recover. NEMTY PROJECT also appends each filename with “.nemty” extension (e.g., it would rename “sample.jpg” to “sample.jpg.nemty” and so on so forth). Additionally, NEMTY PROJECT drops a text file named “NEMTY-DECRYPT.txt” in almost all existing folders.
The created text file delivers a message stating that data is encrypted and that victims have to visit NEMTY PROJECT’s website (located in Tor network) to find decryption instructions. NEMTY PROJECT encrypts data by using an algorithm that generates a unique decryption key individually for each victim. The problem is that keys are stored in a remote server controlled by NEMTY PROJECT’s developers. Therefore, after visiting the site victims will be presented with a ransom-demanding message. In other words, they’ll have to pay for the decryption key/tool. The price is $1000 and the payment must be submitted using Bitcoin cryptocurrency. However, even if you can afford paying, you should never do so. Cyber criminals are notorious for ignoring victims once payments are submitted. For this reason, encouragements to submit payments should be ignored. Unfortunately, there are no tools capable of cracking NEMTY PROJECT’s encryption and restoring data for free. This means that the only thing victims can do is restore everything from a backup.
How did ransomware infect my computer?
The way developers proliferate NEMTY PROJECT is currently unknown. Yet we should still mention that vast majority of ransomware infections are proliferated using spam emails, third party software download sources, fake software updaters/cracks, and trojans. Spam campaigns are used to send hundreds of thousands of deceptive emails that contain malicious attachments (links and/or files), as well as messages encouraging recipients to open them. In order to create the impression of legitimacy and increase the chance of tricking users, crooks present attachments as invoices, bills, receipts, or other important documents. Freeware download websites, free file hosting sites, Peer-to-Peer (P2P) networks (e.g., torrents, eMule, etc.) present malicious executables as legitimate software. By doing so, crooks trick users into manual download/installation of malware. Next go fake updaters and cracks which inject malware rather than serving their actual purpose, which is updating software or providing users with free access to its paid features. Last but not least are trojans, which are essentially malicious lightweight applications designed to infiltrate systems with the intention of injecting additional malware.
| Name | NEMTY PROJECT virus |
| Threat Type | Ransomware, Crypto Virus, Files locker |
| Encrypted Files Extension | .nemty |
| Ransom Demanding Message | NEMTY-DECRYPT.txt, Tor website |
| Ransom Amount | $1000 (in Bitcoins) |
| Cryptowallet Address | 388crtat7DXKc5rWhvBqEVpWM5k9BDtEWo |
| Cyber Criminal Contact | Chat in the Tor website. |
| Detection Names | Acronis (Suspicious), Qihoo-360 (HEUR/QVM20.1.58E9.Malware.Gen), Rising (Trojan.Generic@ML.92 (RDML:gFGPZmPws6vy1JTMN/MWww)), Symantec (ML.Attribute.HighConfidence), Full List Of Detections (VirusTotal) |
| Symptoms | Can’t open files stored on your computer, previously functional files now have a different extension, for example my.docx.locked. A ransom demanding message is displayed on your desktop. Cyber criminals are asking to pay a ransom (usually in bitcoins) to unlock your files. |
| Distribution methods | Infected email attachments (macros), torrent websites, malicious ads. |
| Damage | All files are encrypted and cannot be opened without paying a ransom. Additional password stealing trojans and malware infections can be installed together with a ransomware infection. |
| Removal | To eliminate NEMTY PROJECT virus our malware researchers recommend scanning your computer with Spyhunter. |
| Free scanner checks if your computer is infected. To remove malware, you have to purchase the full version of Spyhunter. |
How to protect yourself from ransomware infections?
Every user should know that the main reasons for computer infections are poor knowledge and reckless behavior. The key to its safety is caution. For this reason, paying attention when browsing the Internet, as well as downloading, installing, and updating software is paramount. It is very important to handle all email attachments with care. Files/links received from suspicious/unrecognizable email addresses should never be opened. Same goes for attachments that are irrelevant and do not concern you. Desired software should be downloaded only from official sources, preferably using direct download links. Keeping installed applications up-to-date is also a must. To achieve this, however, use only implemented functions or tools provided by the official developer. Be aware that third party downloaders, installers and updaters often include rogue application, which is why such tools should never be used. Cracking installed applications should also not be considered, because not only software piracy is a cyber crime, but also the risk of infections is extremely high, due to the fact that vast majority of cracks are fake. Ultimately, be sure to have a reputable anti-virus/anti-spyware suite installed and running at all times – it will help you to detect and eliminate malware before it does any harm. If your computer is already infected with NEMTY PROJECT, we recommend running a scan with Spyhunter for Windows to automatically eliminate this ransomware.
The ransom demand
Like any proper file-encrypting malware, Nemty will delete the shadow copies for the files it processes, taking away from the victim the possibility to recover versions of the data as created by the Windows operating system.Top articles1/5READ MOREApple Releases iOS 12.4.1 to Patch Security Flaw Behind JailbVictims will see a ransom note informing that the attackers hold the decryption key and that data is recoverable for a price.
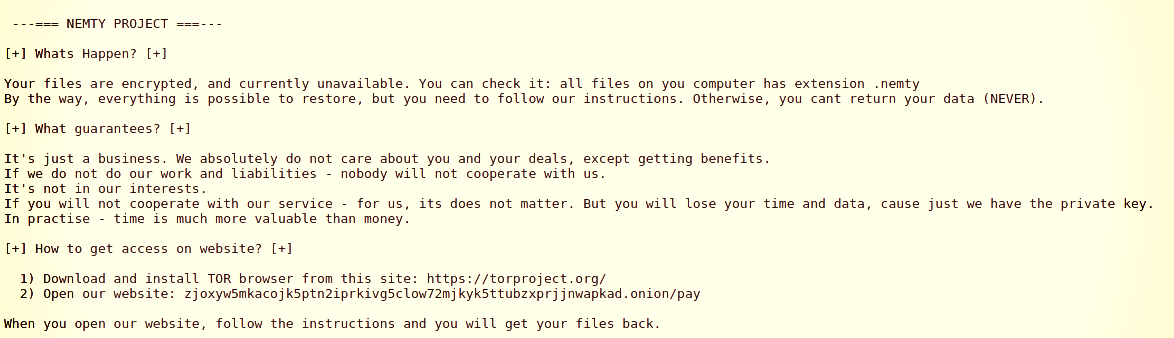
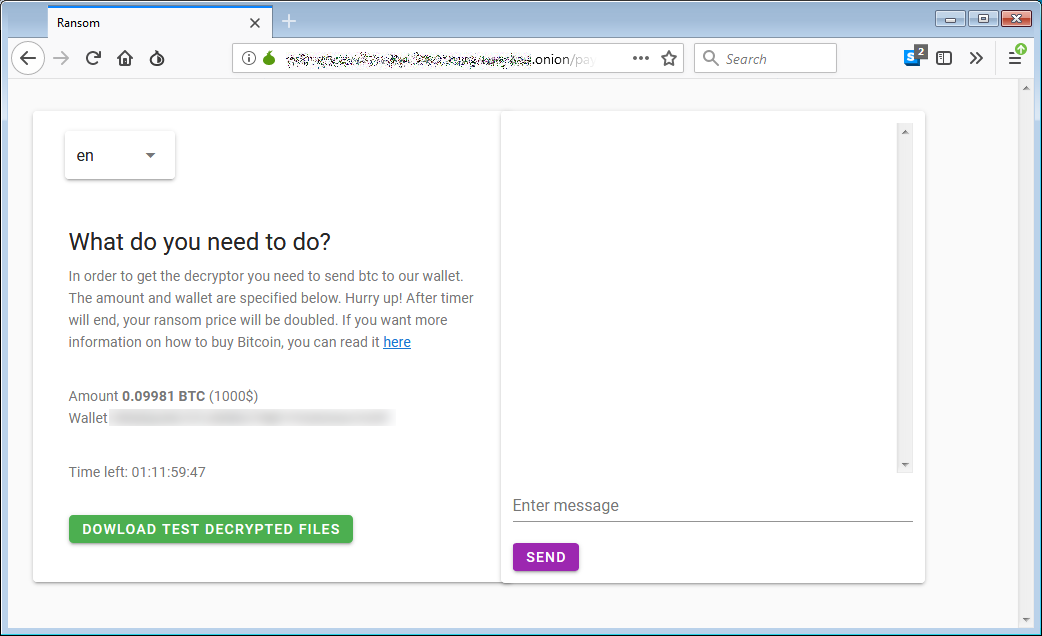
In BleepingComputer’s tests, the ransom demand was 0.09981 BTC, which converts to around $1,000 at the moment.
The payment portal is hosted on the Tor network for anonymity, and users have to upload their configuration file.
Based on this, they are provided with the link to another website that comes with a chat function and more information on the demands.
Messages in the code
Security researcher Vitali Kremez took a closer look at the malware and noticed that it comes with an unusual name for the mutex object. The author called it “hate,” as visible in the image below.
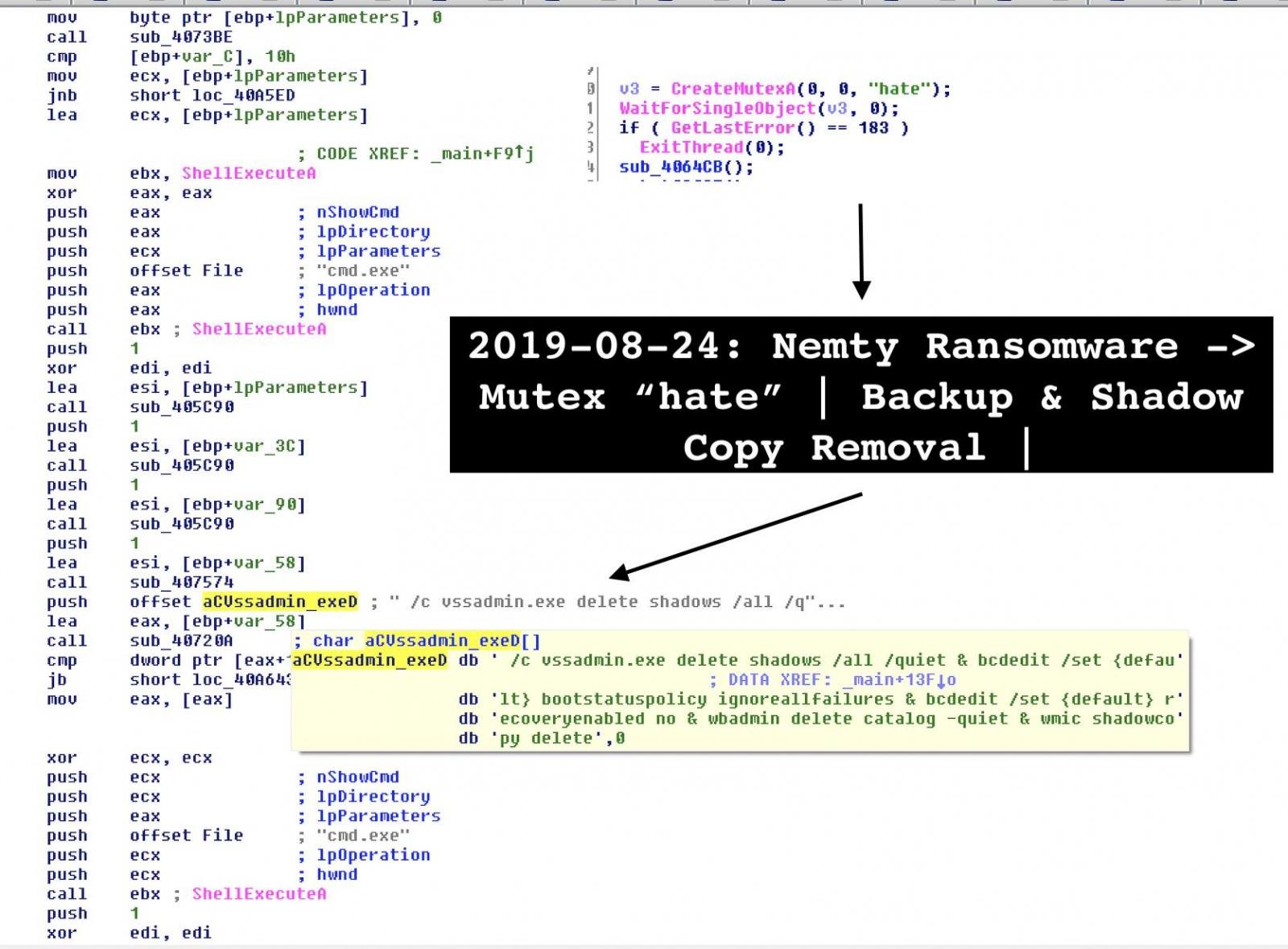
A mutually exclusive (mutex) object is a flag that allows programs to control resources by allowing access to them to one execution thread at a time.
Another weird thing Kremez noticed in Nemty’s code is a link to this picture of Vladimir Putin, with a caption saying “I added you to the list of [insult], but only with pencil for now.”
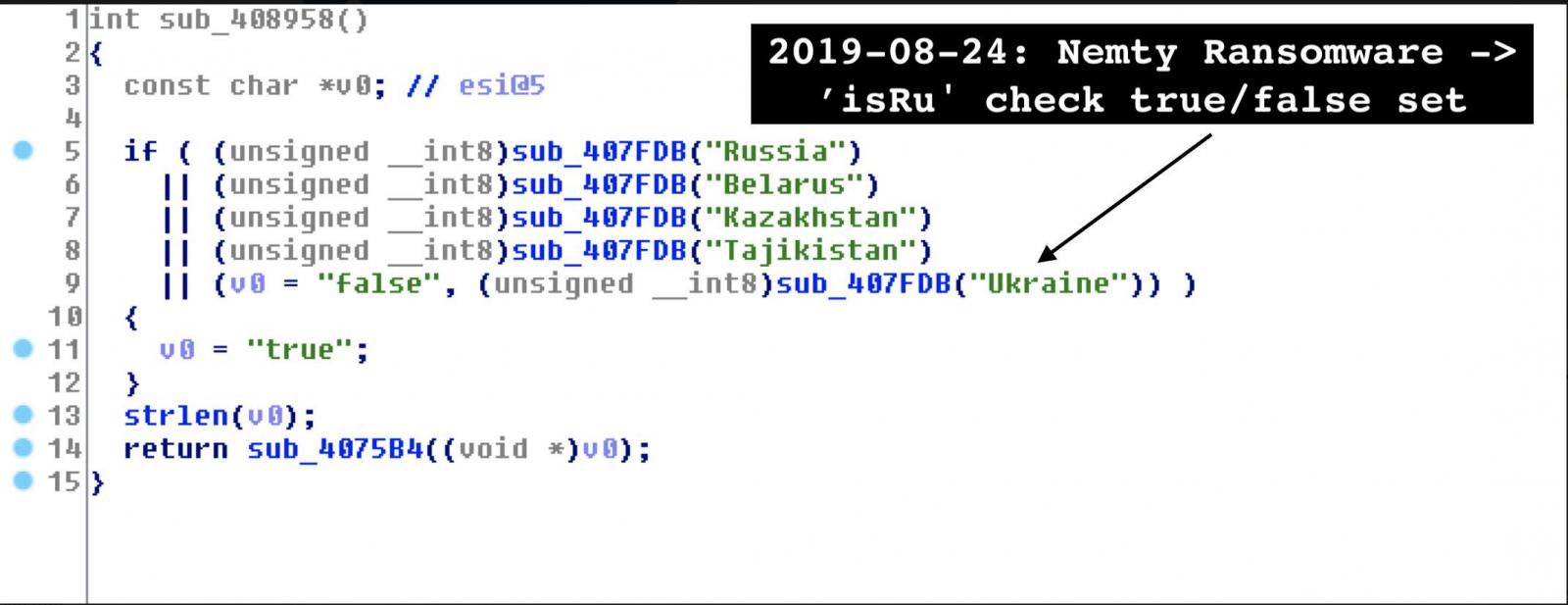
The list of peculiarities does not stop at this. A straight message to the antivirus industry was spotted by the researcher.
At first, the reference seemed an odd thing in the code but a second look at how Nemty worked revealed that it was the key for decoding base64 strings and create URLs is a straight message to the antivirus industry.
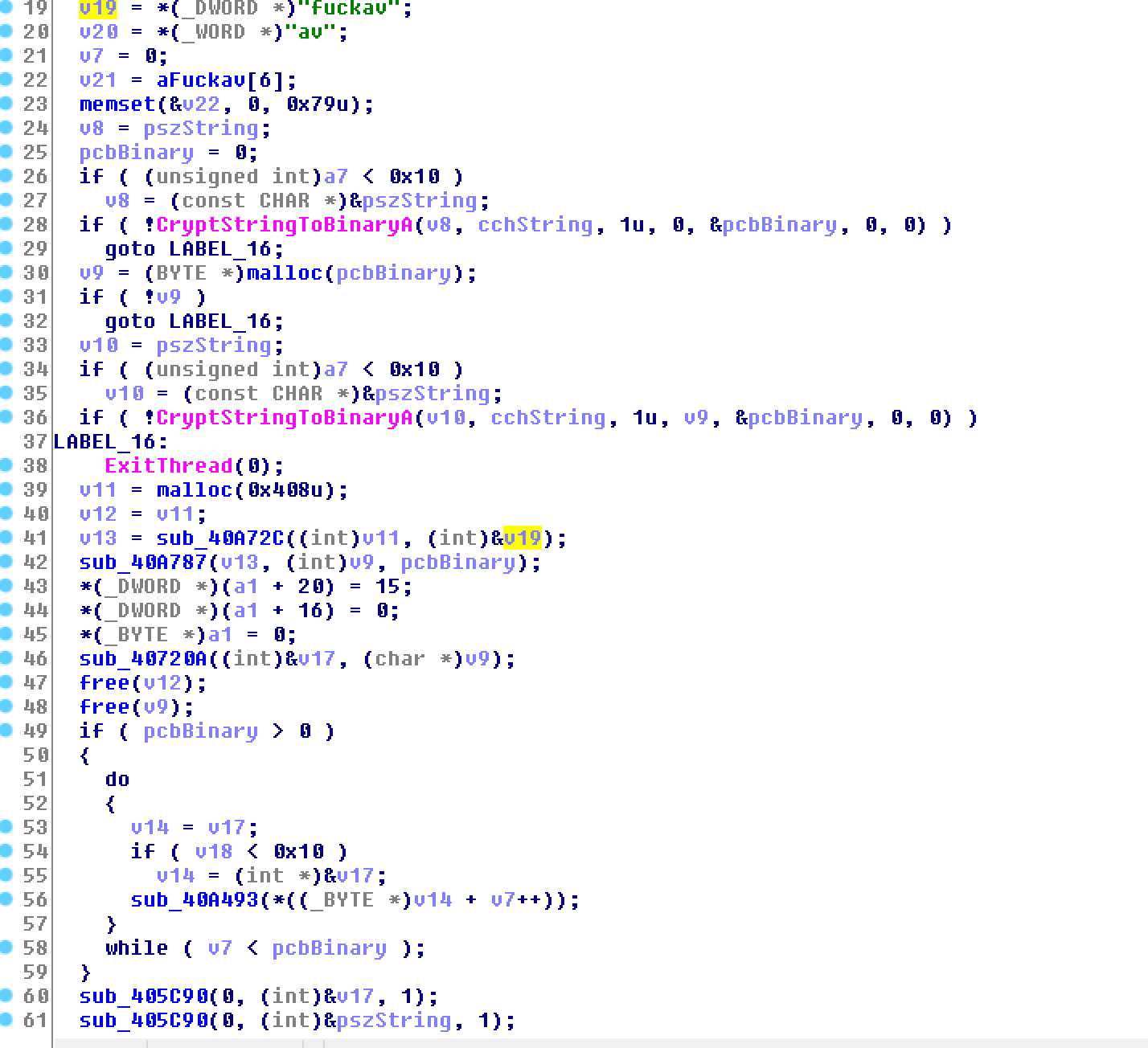
Another interesting thing is a verification Nemty makes to identify computers in Russia, Belarus, Kazakhstan, Tajikistan, and Ukraine. This is not to exempt the hosts from the file encryption routine, though, Kremez told BleepingComputer.
The “isRU” check in the malware code simply marks the systems as being in one of the five countries and then sends to the attacker data that includes the computer name, username, operating system, and computer ID.
It’s unclear how Nemty is distributed but Kremez heard from a reliable source that the operators deploy it via compromised remote desktop connections.Compared to phishing email, which is currently the common distribution method, leveraging a RDP connection puts the attacker in control as they no longer have to wait for the victim to take the phishing bait.Kremez published his research notes on Nemty where he includes the list of folders (anything needed for booting the OS) and the file extensions (binaries, shortcuts, and log data) the malware does not touch.
Remove NEMTY Virus and Try Restoring Files
To remove NEMTY ransomware from your computer, we strongly recommend that you read the instructions underneath. They have been created with the primary purpose to help you remove the NEMTY ransomware files and try to restore all encrypted data. For a faster and effective removal, we strongly recommend that you download and run a scan of your computer using a professional malware removal software. Such program has been made with the main idea to help you erase all traces of the NEMTY ransomware from your machine by scanning for its files and objects. It can also protect you from future threats and intrusive software of this type.
Preparation before removing NEMTY ransomware.
Before starting the actual removal process, we recommend that you do the following preparation steps.
- Make sure you have these instructions always open and in front of your eyes.
- Do a backup of all of your files, even if they could be damaged. You should back up your data with a cloud backup solution and insure your files against any type of loss, even from the most severe threats.
- Be patient as this could take a while.
Step 1: Boot Your PC In Safe Mode to isolate and remove NEMTY ransomware


Step 2: Clean any registries, created by NEMTY ransomware on your computer.
The usually targeted registries of Windows machines are the following:
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunOnce
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce
You can access them by opening the Windows registry editor and deleting any values, created by NEMTY ransomware there. This can happen by following the steps underneath:
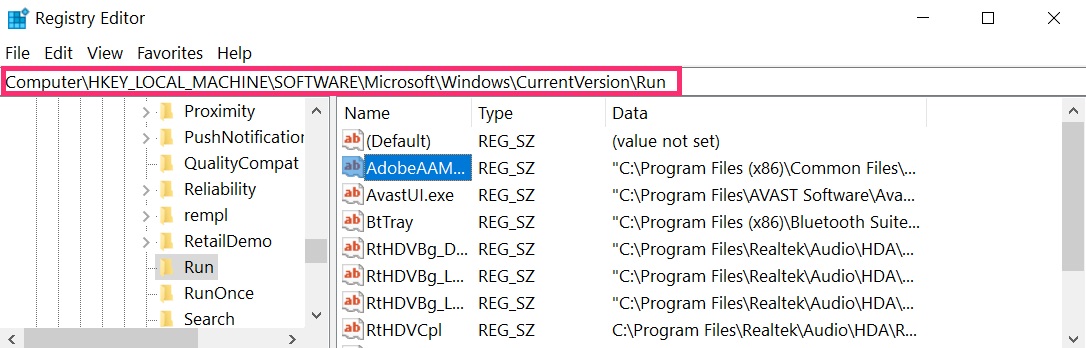
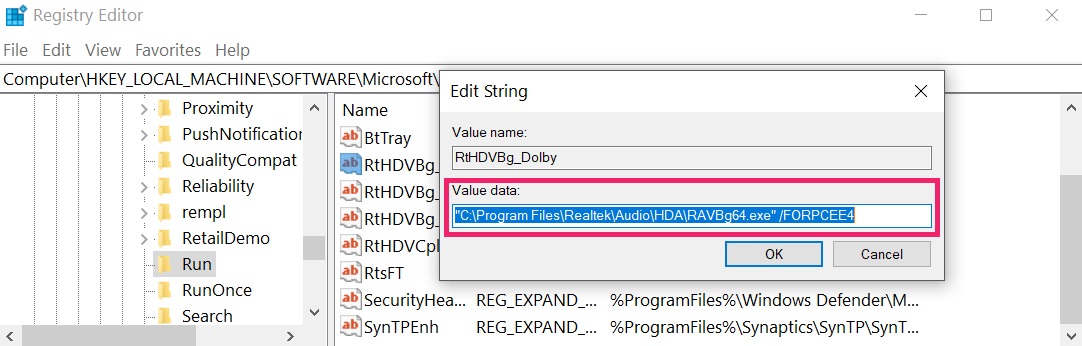 Tip: To find a virus-created value, you can right-click on it and click “Modify” to see which file it is set to run. If this is the virus file location, remove the value.
Tip: To find a virus-created value, you can right-click on it and click “Modify” to see which file it is set to run. If this is the virus file location, remove the value.
Step 3: Find files created by NEMTY ransomware
 For Windows 8, 8.1 and 10.
For Windows 8, 8.1 and 10. For Windows XP, Vista, and 7.
For Windows XP, Vista, and 7.For Newer Windows Operating Systems
1: On your keyboard press + R and write explorer.exe in the Run text box and then click on the Ok button.
2: Click on your PC from the quick access bar. This is usually an icon with a monitor and its name is either “My Computer”, “My PC” or “This PC” or whatever you have named it.
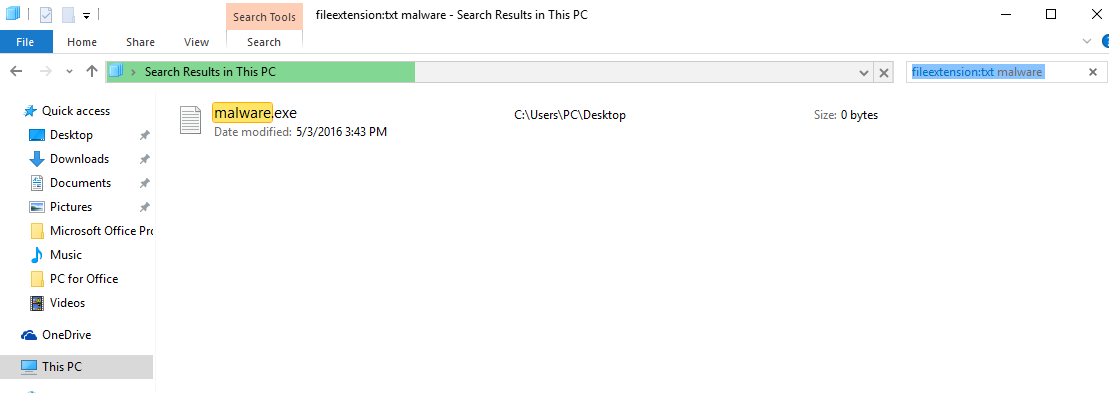
3: Navigate to the search box in the top-right of your PC’s screen and type “fileextension:” and after which type the file extension. If you are looking for malicious executables, an example may be “fileextension:exe”. After doing that, leave a space and type the file name you believe the malware has created. Here is how it may appear if your file has been found:
N.B. We recommend to wait for the green loading bar in the navination box to fill up in case the PC is looking for the file and hasn’t found it yet.
Before starting “Step 4”, please boot back into Normal mode, in case you are currently in Safe Mode.
This will enable you to install and use SpyHunter 5 successfully.
Step 4: Scan for NEMTY ransomware with SpyHunter Anti-Malware Tool

Step 5 (Optional): Try to Restore Files Encrypted by NEMTY ransomware.
Ransomware infections and NEMTY ransomware aim to encrypt your files using an encryption algorithm which may be very difficult to decrypt. This is why we have suggested several alternative methods that may help you go around direct decryption and try to restore your files. Bear in mind that these methods may not be 100% effective but may also help you a little or a lot in different situations.
Method 1: Scanning your drive’s sectors by using Data Recovery software.
Another method for restoring your files is by trying to bring back your files via data recovery software. Here are some suggestions for preferred data recovery software solutions:
- Stellar Data Recovery Technicians License(Pro version with more features)
- Stellar Windows Data Recovery
- Stellar Photo Recovery
Method 2: Trying Kaspersky and EmsiSoft’s decryptors.
If the first method does not work, we suggest trying to use decryptors for other ransomware viruses, in case your virus is a variant of them. The two primary developers of decryptors are Kaspersky and EmsiSoft, links to which we have provided below:
Method 3: Using Shadow Explorer
To restore your data in case you have backup set up, it is important to check for Volume Shadow Copies, if ransomware has not deleted them, in Windows using the below software:
Method 4: Finding the decryption key while the cryptovirus sends it over a network via a sniffing tool.
Another way to decrypt the files is by using a Network Sniffer to get the encryption key, while files are encrypted on your system. A Network Sniffer is a program and/or device monitoring data traveling over a network, such as its internet traffic and internet packets. If you have a sniffer set before the attack happened you might get information about the decryption key.