Troldesh aka Encoder.858 or Shade is a Trojan and a crypto-ransomware variant created in Russia and spread all over the world. Troldesh is based on so-called encryptors that encrypt all of the user’s personal data and extort money to decrypt the files. Troldesh encrypts a user’s files with a “.xtbl” extension. Troldesh is spread initially via e-mail spam. A distinctive feature of the Troldesh attack is direct communication with the victim. While most Ransom-Trojan attackers try to hide and avoid any direct contact, Troldesh’s creators provide their victims with an e-mail address. The attackers use this email correspondence to demand a ransom and dictate a payment method.
Discovery of Trodlesh ransomware
The events that took place in Troldesh are massive: it was registered on November 1, 2018 (on behalf of a large bank). February was marked by a leapfrog from the brands: Troldesh pretended to be all contractors. In 2000, mailings per day and they are continued. Kroltolker Troldesh in this campaign not only encrypts. While you save money for decryption, you get your master crypt. The fact that we have cryptographic functions, In addition, from the infected computer, it sends itself further new mailing technique is used. Usually, in Troldesh there is a wide list of companies in various industries – retail, wholesale, oil and gas, construction. Letters from top managers.
Unlike the early tricks of the cryptographer, the letters were written and executed correctly. Usually, look like mailing banking Trojans. In the mailing involved a fairly large-scale infrastructure. So, as a rule, the black market operates on the market, where it is easier and cheaper to use the services of someone who owns a network of hundreds and thousands of different devices controlled by him (no matter what). The owner of a botnet network, issues related to the delivery of malware.
Troldesh is a cryptographer requiring money to decrypt files. The Troldesh cryptology encrypts files in an infected form and requires payment from the user to restore access to the information. In Group-IB it is reported that Troldesh is the most popular cryptographer lately, with the result of work on the response team, Group-IB (incident response) has been confronted in at least 7 incidents in 2018.
Process of Troldesh Ransomware
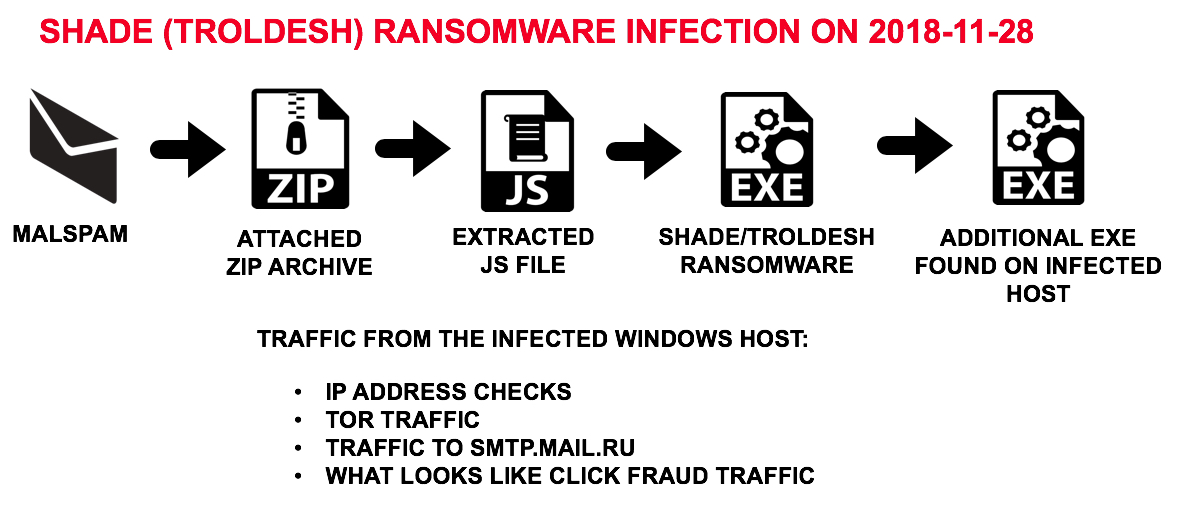
How Troldesh ransomware spreads?
Troldesh was first recognized in 2014 and since then it is playing hide and seek. The vector has majorly come into the play with malspam like phishing attacks. Hackers are sending malicious email attachments and links to target people.
The malware itself is offered as a download in a corrupted zip file. When the user accesses the file or performs the download, then JavaScript also downloads the malicious payload along with it. The payload is mostly hosted on websites with the compromised CMS (Content Management System).
The Shade emails are often spoofed. The Troldesh target uses a phishing campaign to target the victims. As the ransom notes of Troldesh is written in English & Russian, so the origin of Shade is considered as Russian. Mostly shade is interested in Windows Operating System.
If you have received the malicious attachment or Shade link in your email and you haven’t unzipped the file then you won’t become a victim. To get infected, you need to unzip the zip by double-clicking on the JavaScript file.
What Are the Symptoms of Troldesh ransomware?
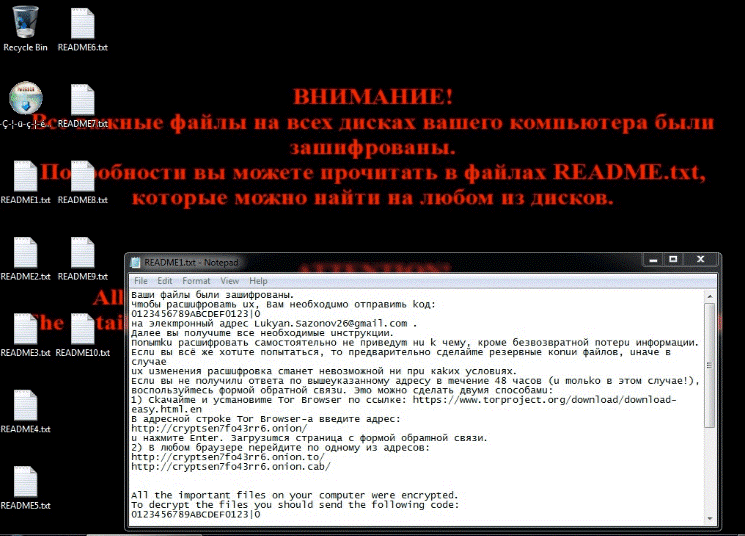
Once the Troldesh ransomware is installed on the system, it drops the end number of readme files (.txt files) on the same machine. After following the encryption process, the motive of shade to ensure the user/victim is reading the ransom message. These files contain the same ransom notes in each file.
The normal targeted file extension are like .odm, .j2c, .asm, .m1v, .j2k, .iqy, .jps, .ods, .odb, .obj, .potm, .pdd, .pot, .dpx, .ics, .icb, .php5, .pcx, .slk, .shtml, .sdpx, .tbx, .wpd, .wmv, .wml, .wim, .vtml, .vtx, .wav, .wbm, .wbmp, .vsd, .vtm, .vst, .vrp, .wmf, .dc3, .tiff, .tbk, .vcs, .torrent, .tdi, .u3d, .tld, .thmx, .tif, .asmx, .avs, .asa, .arw, .asx, .avs, .backup, .as, .db, .djvu, .dcm, .dc3, .dat, .doc, .dib, .docm, .dbx.
How Does Encryption of Troldesh Ransomware Work?
All the files are encrypted by using the AES 256 in Cipher Block Chaining mode. For each encrypted file, there are two random 256-bit AES keys that are generated. The first key is used for file content, wherein the second encryption key is used for encrypting the name of the file. All the above-mentioned extension names are added after then encryption of the filename.
How to Prevent Troldesh Ransomware?
As precaution is always better than the cure, it is recommended to take the required security measure to prevent such attacks.
- Always take a backup of your vital files.
- Keep your system and software updated because updating your tool on regular bases can easily help you to plug up vulnerabilities.
- Before access or downloading the attachments, it is important to scan the emails and the attached links.
- Use anti-malware and antivirus tools.
- Blacklist wscript.exe. usually does not require users to run scripts. So, you can use the blacklisting feature to ensure your safety.
- Conduct Cybersecurity training programs. Awareness of the latest threat and attacks helps you to protect your machine by patching the loopholes. Owner of the organization should conduct training programs or informative email to its employees to stay safe.
