The extremely popular UC Browser and UC Browser Mini Android applications with a total of over 600 million installs expose their users to MiTM attacks by downloading and installing extra modules from their own servers using unprotected channels and bypassing Google Play’s servers altogether.
According to a Google support document regarding Google Play “Privacy, Security, and Deception“, Android apps “distributed via Google Play may not modify, replace, or update itself using any method other than Google Play’s update mechanism. Likewise, an app may not download executable code (e.g. dex, JAR, .so files) from a source other than Google Play.”
“Anyone who has installed this software may be in danger. Doctor Web has detected its hidden ability to download auxiliary components from the Internet,” as detailed in Doctor Web’s analysis. “The browser receives commands from the command and control server and downloads new libraries and modules, which add new features and can be used to update the software.”
Exposes users to MitM attacks
While the UC Browser and UC Browser Mini haven’t yet been seen downloading and installing malicious code on the devices where it has been installed, given that it can download and install extra modules from its servers exposes users to potential risks.
As Doctor Web’s research team explains in the report, “It’s impossible to be sure that cyber criminals will never get ahold of the browser developer’s servers or use the update feature to infect hundreds of millions of Android devices.”
Pushing Malicious UC Browser Plug-ins Using MiTM Attack
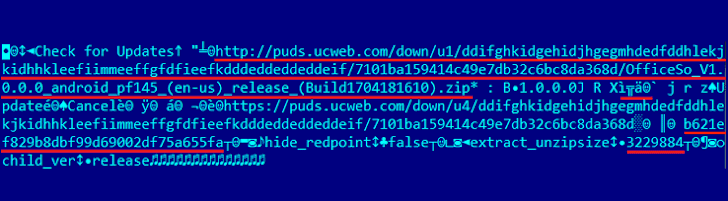
It turns out that the reported feature downloads new plugins from the company server over insecure HTTP protocol instead of encrypted HTTPS protocol, thus allowing remote attackers to perform man-in-the-middle (MiTM) attacks and push malicious modules to targeted devices.
Since UC Browser works with unsigned plug-ins, it will launch malicious modules without any verification,” the researchers say.
“Thus, to perform an MITM attack, cyber criminals will only need to hook the server response from http://puds.ucweb.com/upgrade/index.xhtml?dataver=pb, replace the link to the downloadable plug-in and the values of attributes to be verified, i.e., MD5 of the archive, its size, and the plug-in size. As a result, the browser will access a malicious server to download and launch a Trojan module.”
Doctor Web’s security researchers also created a MiTM attack demo video (embedded below), showing how a potential victim wants to view a PDF document using UC Browser and has to download a plug-in module to do it from the app’s update servers.
The researchers intercept the message sent to the update server and replace the module with a specially crafted one designed to display a “PWNED!” message on the victim’s device.
