Masodas may be appear as new computer threat but in reality, this is just a remake of other ransomware from STOP family of malware. The name was derived from the extension that this threat is appending to all infected files and that is .masodas.Masodas is a high-risk ransomware-type infection designed to infiltrate computers and encrypt most of stored files. While doing so, Masodas appends filenames each filename with “.masodas” extension (thus its name).
This ransomware that is attacking computers worldwide do not have a direct target. Normally, the carriers of Masodas are spread in various ways and hitting random computer users that were entices by its bait. Spam emails, aggressive advertisements, pirated apps, and malicious links from various locations are known sources of infection where careless users are in the forefront. Opening the email attachment or downloading advertised software instantly runs Masodas and right at this moment, other payloads of this threat unleashes together on the infected computer.
Like other ransomware from the group including Vesrato and Nuksus, this new variant aims on locking files on the computer and makes it unavailable to user. Masodas can achieve this task by searching the infected computer’s drive for common files and applies a complex encryption method on them. Afterwards, the ransomware modifies the file name and adds .Masodas suffix probably as show-off that it has infected majority of user’s data. This incident is an ideal timing for attackers to demand money from victims. Remittance payment serves as compensation for the private key and Masodas decryption software, which are crucial to restore the files to its original format.
In most ransomware topics and discussion, security specialist states that paying the cyber criminals is a risky option because it is not a guarantee that the offending party will send the key and decryption tool. If ever victims successfully obtained them after making the payment, there is no assurance that all files can be restored with the provided items.
Example
example 1
For example, document.doc will become document.doc.mosodas after the contamination. This renaming process is actually the lighter side of the infection. What is more damaging is the encryption method that Masodas applies to majority of files that are valuable to users like documents, spreadsheets, photos, images, videos, movies, archives, databases, and so on.
example 2
For example, it would rename “sample.jpg” to “sample.jpg.masodas” and so on so forth. Once data is encrypted, Masodas drops “_readme.txt” file in almost all existing folders. This ransomware belongs to Djvu family and it was firstly discovered by Michael Gillespie.
How did the Masodas ransomware get on my computer?
The Masodas ransomware is distributed via spam email containing infected attachments or by exploiting vulnerabilities in the operating system and installed software.
Cyber-criminals spam out an email, with forged header information, tricking you into believing that it is from a shipping company like DHL or FedEx. The email tells you that they tried to deliver a package to you, but failed for some reason. Sometimes the emails claim to be notifications of a shipment you have made. Either way, you can’t resist being curious as to what the email is referring to – and open the attached file (or click on a link embedded inside the email). And with that, your computer is infected with the Masodas ransomware.
Masodas ransomware was also observed attacking victims by hacking open Remote Desktop Services (RDP -Remote Desktop Protocol) ports. The attackers scan for the systems running RDP (TCP port 3389) and then attempt to brute force the password for the systems.
What is Masodas ransomware?
- Ransomware family: STOP (DJVU) ransomware
- Extensions: Masodas
- Ransomware note: _readme.txt
- Ransom: From $490 to $980 (in Bitcoins)
- Contact: gorentos@bitmessage.ch, gorentos2@firemail.cc, or @datarestore on Telegram
The Masodas ransomware restricts access to data by encrypting files. It then attempts to extort money from victims by asking for “ransom”, in the form of Bitcoin cryptocurrency, in exchange for access to data. This ransomware targets all versions of Windows including Windows 7, Windows 8 and Windows 10. When this ransomware is first installed on your computer it will create a random named executable in the %AppData% or %LocalAppData% folder. This executable will be launched and begin to scan all the drive letters on your computer for data files to encrypt.
Masodas ransomware searches for files with certain file extensions to encrypt. The files it encrypts include important productivity documents and files such as .doc, .docx, .xls, .pdf, among others. When these files are detected, this infection will change the extension to Masodas, so they are no longer able to be opened.
Files targeted are those commonly found on most PCs today; a list of file extensions for targeted files include:
.sql, .mp4, .7z, .rar, .m4a, .wma, .avi, .wmv, .csv, .d3dbsp, .zip, .sie, .sum, .ibank, .t13, .t12, .qdf, .gdb, .tax, .pkpass, .bc6, .bc7, .bkp, .qic, .bkf, .sidn, .sidd, .mddata, .itl, .itdb, .icxs, .hvpl, .hplg, .hkdb, .mdbackup, .syncdb, .gho, .cas, .svg, .map, .wmo, .itm, .sb, .fos, .mov, .vdf, .ztmp, .sis, .sid, .ncf, .menu, .layout, .dmp, .blob, .esm, .vcf, .vtf, .dazip, .fpk, .mlx, .kf, .iwd, .vpk, .tor, .psk, .rim, .w3x, .fsh, .ntl, .arch00, .lvl, .snx, .cfr, .ff, .vpp_pc, .lrf, .m2, .mcmeta, .vfs0, .mpqge, .kdb, .db0, .dba, .rofl, .hkx, .bar, .upk, .das, .iwi, .litemod, .asset, .forge, .ltx, .bsa, .apk, .re4, .sav, .lbf, .slm, .bik, .epk, .rgss3a, .pak, .big, wallet, .wotreplay, .xxx, .desc, .py, .m3u, .flv, .js, .css, .rb, .png, .jpeg, .txt, .p7c, .p7b, .p12, .pfx, .pem, .crt, .cer, .der, .x3f, .srw, .pef, .ptx, .r3d, .rw2, .rwl, .raw, .raf, .orf, .nrw, .mrwref, .mef, .erf, .kdc, .dcr, .cr2, .crw, .bay, .sr2, .srf, .arw, .3fr, .dng, .jpe, .jpg, .cdr, .indd, .ai, .eps, .pdf, .pdd, .psd, .dbf, .mdf, .wb2, .rtf, .wpd, .dxg, .xf, .dwg, .pst, .accdb, .mdb, .pptm, .pptx, .ppt, .xlk, .xlsb, .xlsm, .xlsx, .xls, .wps, .docm, .docx, .doc, .odb, .odc, .odm, .odp, .ods, .odt
Once your files are encrypted with the Masodas extension, this ransomware will create the _readme.txt file ransom note in each folder that a file has been encrypted and on the Windows desktop. These files are located in every folder that a file was encrypted and contain the information on how to contact the cybercriminals and get your files back.
When the infection has finished scanning your computer it will also delete all of the Shadow Volume Copies that are on the affected computer. It does this so that you cannot use the shadow volume copies to restore your encrypted files.
Which Files May Get Affected by Masodas Virus Ransomware?
- Masodas Virus Ransomware serves as a typical file-encoding Trojan. As soon as it gets access to your machine, this crypto malware will perform a quick scan to find the paths to all of your personal files. The targeted data includes all MS Office documents, your precious photos and videos, your databases, the program files, etc. Only a few files such as the ones related to the core Windows processes may be spared. Once the operation ends, you will notice a threatening lockdown message on your desktop. The cyber criminals give the victims only several days to pay the ransom of Bitcoins, or else they threaten to delete the decryption key. The purpose of this frightening message is to shock the person and make him act irrationally. The victims often feel as the only solution to the issue is to pay the money. In reality, all specialists unanimously recommend not to follow the instructions of the hackers for several different reasons.
Masodas Virus usually drops a ransom note file with a ransom message and places it somewhere easy to locate. It aims to ask you to pay BitCoin or other crypto so that your files can work once more. Then, the Masodas Virus virus may attack files with the following file types to encrypt them:
- Videos.
- Images.
- Documents.
- Audio files.
- Archives.
After Masodas Virus encrypts the files, the virus leaves the files no longer able to be opened and likely appends its own file extenson to them.
Is my computer infected with Masodas Ransomware?
When this ransomware infects your computer it will scan all the drive letters for targeted file types, encrypt them, and then append the Masodas extension to them. Once these files are encrypted, they will no longer able to be opened by your normal programs. When this ransomware has finished encrypting the victim’s files, it will also display a ransom note that includes instructions on how to contact these cybercriminals (gorentos@bitmessage.ch or gorentos2@firemail.cc).
This is the message that the Masodas ransomware (_readme.txt) will display:
ATTENTION! Don’t worry, you can return all your files!
All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-o7ClqIH7RS
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that’s price for you is $490.
Please note that you’ll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don’t get answer more than 6 hours.To get this software you need write on our e-mail:
gorentos@bitmessage.chReserve e-mail address to contact us:
gorentos2@firemail.ccOur Telegram account:
@datarestore
Mark Data RestoreYour personal ID:
4. Is it possible to decrypt files encrypted with the Masodas ransomware?
If your file were encrypted using an offline key (How do I know if I was infected with an offline key?) there is a chance you can recover your files by using the STOPDecrypter decryption tool.
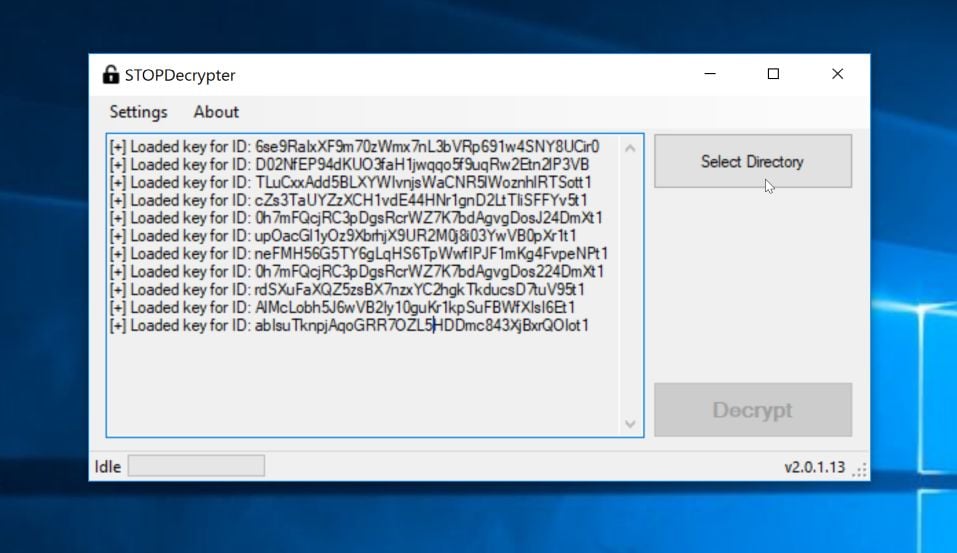
Unfortunately, in most cases, it’s not possible to recover the files encrypted by this ransomware because the private key which is needed to unlock the encrypted file is only available through the cybercriminals.
There is no guarantee that if you pay the ransom your files will be recovered, furthermore, this will encourage these bad guys to continue and even expand their operations. We strongly recommend that you do not pay the ransom and instead address the law enforcement agency in your country to report this attack.
Removal Instructions for Masodas Virus
If you want to remove Masodas Virus, we strongly recommend that you first backup your data, just in case something goes wrong. Then, you can follow the manual or automatic removal instructions below, depending on which type of steps suits you more. If you lack the experience and the confidence that you will remove Masodas Virus manually, then you should do what most experts would and save yourself some time by downloading and running a scan with an advanced anti-malware software. Such programs are created to quickly identify and remove threats and programs with intrusive behaviour, like Masodas Virus, plus they also aim to ensure that your system is protected against future intrusions as well.
The main reasons not to pay the ransom are two. First, you may not receive the promised unlocking key even after doing exactly as the hackers demand. They often scam the victims because the Bitcoin platform doesn’t allow refunds and the people have no way to get their money back. The second reason not to finance cyber criminals is that your money will only motivate them to create more aggressive ransomware like Masodas Virus. On the other hand, if their attacks are in vain, they may stop spamming the web with such malicious Trojans. These parasites require quite some efforts to be created professionally and spread efficiently.
Once you decide not to pay the ransom, there are several other ways that may help you decrypt your personal files. You should begin the attempts by removing all traces of the malware. If you fail to delete Masodas Virus Ransomware properly, it may decrypt your files once again in the future or spread to other connected devices. The manual removal is not the recommended solution since it requires expert-level knowledge in computers. The most reliable tactic is to use dedicated security software that has added FMasodas Virus Ransomware to its database. Once the scan finishes, you should try some of the programs for restoration of files or the integrated System Restore feature. If you are lucky enough to have a spare copy of your files on some external device, you can import them back to your computer safely.
Preparation before removal of Masodas Virus:
1. Make sure to backup your files.
2. Make sure to have this instructions page always open so that you can follow the steps.
3. Be patient as the removal may take some time.
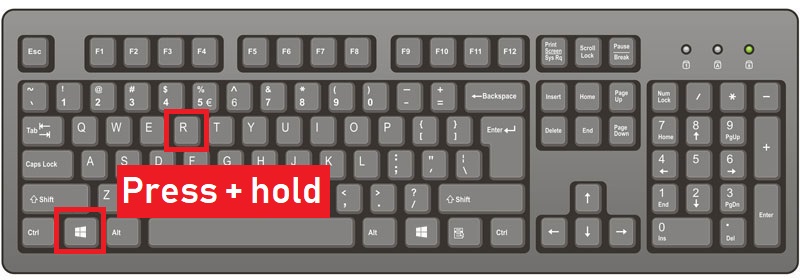
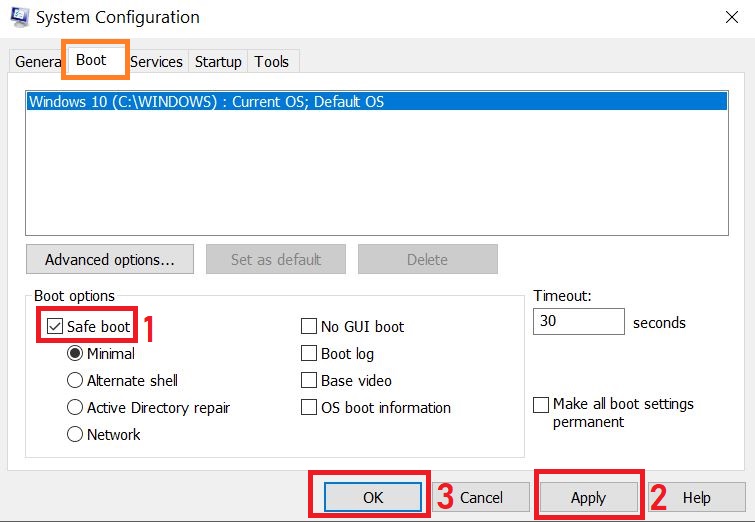
Step 1: Reboot your computer in Safe Mode:
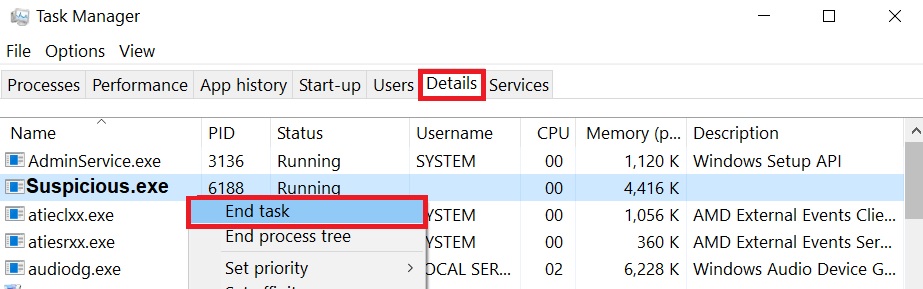
Step 2: Cut out Masodas Virus in Task Manager
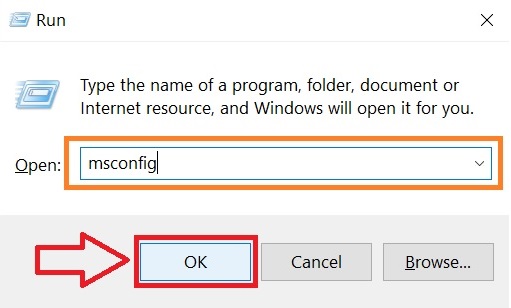
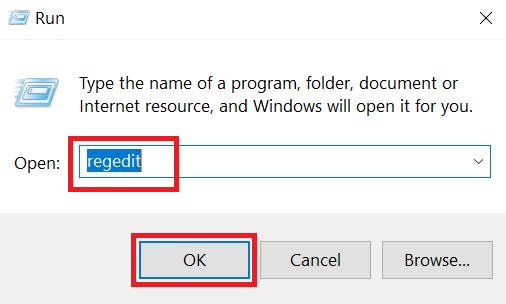
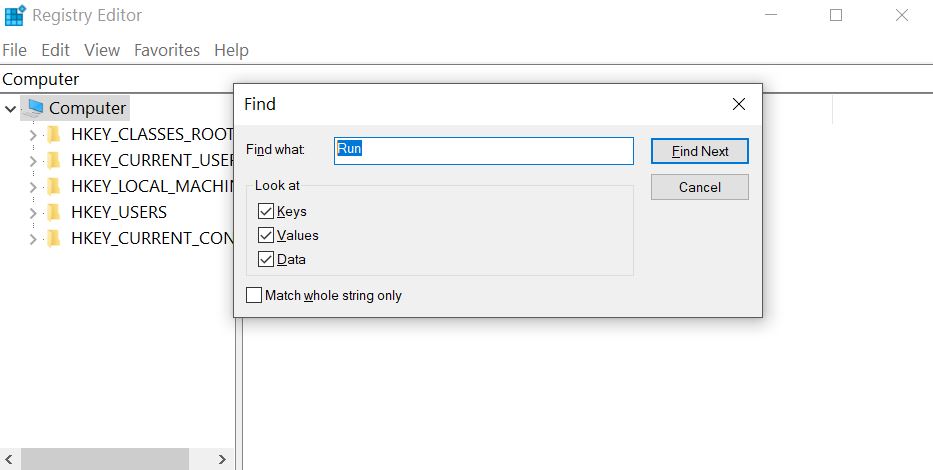
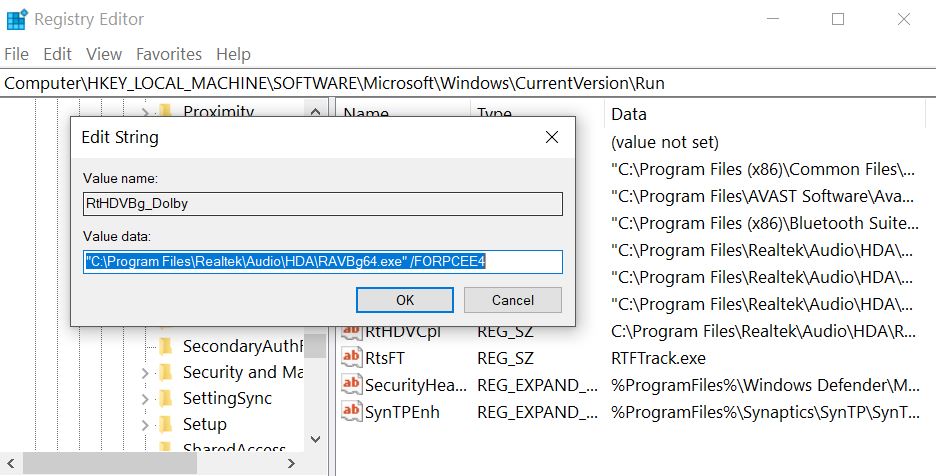
Step 3: Eliminate Masodas Virus‘s Malicious Registries.
For most Windows variants:
Step 4: Scan for and remove all virus files, related to Masodas Virus and secure your system.
Step 5:Recover files encrypted by the Masodas Virus Ransomware.